Let's learn about Networking via these 93 free stories. They are ordered by most time reading created on HackerNoon. Visit the /Learn Repo to find the most read stories about any technology.
1. Accessing Network Apps Running Inside WSL2 from Other Devices in Your LAN
 In this article, I explain how to tweak Windows and WSL networking to bypass WSL NAT and connect to development servers inside WSL from other devices in LAN.
In this article, I explain how to tweak Windows and WSL networking to bypass WSL NAT and connect to development servers inside WSL from other devices in LAN.
2. Cracking the SANS GSEC Certification
 The SANS GIAC Security Essentials (GSEC) certification is for anyone working in the field of Information Security.
The SANS GIAC Security Essentials (GSEC) certification is for anyone working in the field of Information Security.
3. DNS Queries Explained
 DNS is a topic often considered difficult to understand, but the basic workings are actually not hard to grasp. The first fundamental point to grasp is that every domain in existence is linked to an Internet Protocol (IP) address.
DNS is a topic often considered difficult to understand, but the basic workings are actually not hard to grasp. The first fundamental point to grasp is that every domain in existence is linked to an Internet Protocol (IP) address.
4. Clubhouse Is Just LinkedIn Built Better
 LinkedIn may have been the center of business relations for the past decade, but Clubhouse is the Next Gen networking tool we've all been waiting for.
LinkedIn may have been the center of business relations for the past decade, but Clubhouse is the Next Gen networking tool we've all been waiting for.
5. The Top 6 Serial over Network utility
 Attempting to connect a serial device to more than one computer would lead to a tangle of cables and is almost impossible without a serial over network solution
Attempting to connect a serial device to more than one computer would lead to a tangle of cables and is almost impossible without a serial over network solution
6. The Freelance Revolution: Where to Find the Best Freelancers in Tech
 The Most Famous Freelance Skill Destinations: Between Urban Myths and Business Reality
The Most Famous Freelance Skill Destinations: Between Urban Myths and Business Reality
7. How To Modernize IBM i System
 IBM i has evolved overtime and organizations are modernizing their existing legacy systems to use the latest updates in IBM i. It is generally considered as old, obsolete and not trending just because it is in existence since 30 years. But replacing IBM i with some other technology is not worth it, instead IT teams must plan to modernize the existing IBM i systems of their organization. Now, modernizing is not as easy as it looks because the confusion here is which approach to choose among numerous options to update IBM i. The way you modernize your IBM I systems will decide the return you get after the updates. Some of the recommendations include unfolding the data and logic, improving the user interface and the software development process.
IBM i has evolved overtime and organizations are modernizing their existing legacy systems to use the latest updates in IBM i. It is generally considered as old, obsolete and not trending just because it is in existence since 30 years. But replacing IBM i with some other technology is not worth it, instead IT teams must plan to modernize the existing IBM i systems of their organization. Now, modernizing is not as easy as it looks because the confusion here is which approach to choose among numerous options to update IBM i. The way you modernize your IBM I systems will decide the return you get after the updates. Some of the recommendations include unfolding the data and logic, improving the user interface and the software development process.
8. Getting Your IP From Anywhere
 There are several circumstances where you need to know the IP of your current machine.
There are several circumstances where you need to know the IP of your current machine.
9. 4 Certifications to Help You Become an Enterprise Architect
 It can be hard to secure an enterprise architect role. Here are some certificates to help you make a good impression.
It can be hard to secure an enterprise architect role. Here are some certificates to help you make a good impression.
10. You Should Participate in Hackathons; and Here's Why
 Why should you attend hackathons?
Five benefits of attending hackathons
Why should you attend hackathons?
Five benefits of attending hackathons
11. Bridging the Gap Between Technical & Non-technical Teams
 To a certain extent, this gap is caused by a relatively low priority that soft skills are given among tech employees.
To a certain extent, this gap is caused by a relatively low priority that soft skills are given among tech employees.
12. Social-as-a-Service Concept
 “There are only two ways to make money in business: one is to bundle; the other is unbundle.” — Jim Barksdale, former CEO and President of Netscape.
“There are only two ways to make money in business: one is to bundle; the other is unbundle.” — Jim Barksdale, former CEO and President of Netscape.
13. How to Get the PR Ball Rolling
 There comes a time in every business’s living cycle when the company turns to public relations. How to Get that Ball Rolling?
There comes a time in every business’s living cycle when the company turns to public relations. How to Get that Ball Rolling?
14. Lightning Network Could be a Tool to Overcome Limitations
 Lightning Network is a payment protocol operating on blockchains. Allows instant transactions between participating nodes and is proposed as a solution to the bitcoin scalability problem. The Lightning Network is made up of nodes and bidirectional payment channels.
Lightning Network is a payment protocol operating on blockchains. Allows instant transactions between participating nodes and is proposed as a solution to the bitcoin scalability problem. The Lightning Network is made up of nodes and bidirectional payment channels.
15. A Deeper Look into SSH and X.509 Certificates
 Although SSH certificates are the most secure way to regulate SSH access, they are underutilized. This article explains why you should be using SSH certificates
Although SSH certificates are the most secure way to regulate SSH access, they are underutilized. This article explains why you should be using SSH certificates
16. Code Isn't the Only Solution; and 8 Other Dev Lessons, 7 Years Later
 I'm working as a software developer for 7 years. You can read my background and how I got into the industry here. There are a few things I wish I learned earlier. Knowing these in advance would have made my job a lot easier. Some of this might sound pretty obvious, but not for me. If you're in the early stages of your career, doing a few of this will make you stand out.
I'm working as a software developer for 7 years. You can read my background and how I got into the industry here. There are a few things I wish I learned earlier. Knowing these in advance would have made my job a lot easier. Some of this might sound pretty obvious, but not for me. If you're in the early stages of your career, doing a few of this will make you stand out.
17. "DNS Propagation" Does Not Exist: A Suggested Change In Terminology
18. Networking is Not Working
 Let’s face it, networking is hyper-popular. Just open Eventbrite and you will see thousands of business events until the end of 2020. Even now, in the time of pandemic, nobody stopped attending NETWORKING events. Instead, we gladly filled our calendars with online events, webinars, business breakfasts via Zoom not to miss the precious chance to meet a (yet another) new person. Networking promises to bring endless opportunities, partnerships, and a lot of fun, but in fact it often results in nothing except for the senseless waste of time.
Let’s face it, networking is hyper-popular. Just open Eventbrite and you will see thousands of business events until the end of 2020. Even now, in the time of pandemic, nobody stopped attending NETWORKING events. Instead, we gladly filled our calendars with online events, webinars, business breakfasts via Zoom not to miss the precious chance to meet a (yet another) new person. Networking promises to bring endless opportunities, partnerships, and a lot of fun, but in fact it often results in nothing except for the senseless waste of time.
19. Network Security 101: Everything You Need to Know
 Network Security is Vital. Its purpose is to prevent unauthorized users from accessing an organization's network and devices. It is intended to keep data safe.
Network Security is Vital. Its purpose is to prevent unauthorized users from accessing an organization's network and devices. It is intended to keep data safe.
20. Deep Dive into SSL certificates
 A deep dive discussion on SSL certificate
A deep dive discussion on SSL certificate
21. What is community management?
 Communities thrive today because the various reasons people join or form them are being met. These results are even enhanced when there is someone to handle the community management squarely.
Communities thrive today because the various reasons people join or form them are being met. These results are even enhanced when there is someone to handle the community management squarely.
22. Developer Marketing Guide: 2020 Version
 Initial Thoughts
Initial Thoughts
23. How to Build and Grow a Professional Network
 In the professional world, your network is your biggest asset in creating or securing those career opportunities.
In the professional world, your network is your biggest asset in creating or securing those career opportunities.
24. How to do API Caching with Dio and Hive in Flutter
 With this short guide you can add caching to your flutter app that requests an API or a web server and receives information that is required to be stored.
With this short guide you can add caching to your flutter app that requests an API or a web server and receives information that is required to be stored.
25. How to Create a Personal Residential Proxy to Bypass Geo Restrictions
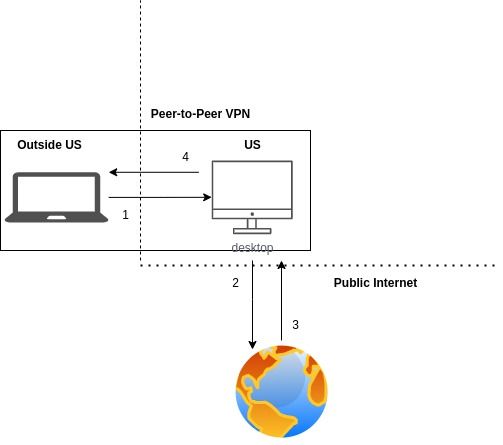 By setting up a peer-to-peer(P2P) VPN and connecting my laptop and desktop to it, I was able to route the traffic of my laptop in India to my desktop in the US.
By setting up a peer-to-peer(P2P) VPN and connecting my laptop and desktop to it, I was able to route the traffic of my laptop in India to my desktop in the US.
26. How to Hack a Huge Career in Tech with PR Expert & Founder Sarah Evans
 I sat down with Sarah Evans—tech industry PR legend and strategic communications startup founder—to talk all things branding and influence: from personal to B2B. You can watch the Youtube version of this podcast right here in this post, or grab the audio-only on Spotify, or over at podcast.hackernoon.com.
I sat down with Sarah Evans—tech industry PR legend and strategic communications startup founder—to talk all things branding and influence: from personal to B2B. You can watch the Youtube version of this podcast right here in this post, or grab the audio-only on Spotify, or over at podcast.hackernoon.com.
27. Networking & Kubernetes: Book Review and Interview with Author James Strong
 Co-author James Strong talks about his book Networking & Kubernetes, published by O'Reilly Media. Strong wrote the book with Vallery Lancey.
Co-author James Strong talks about his book Networking & Kubernetes, published by O'Reilly Media. Strong wrote the book with Vallery Lancey.
28. From Mobile Phones to Networking: Nokia's Evolution in the Tech Industry
 Nokia, once the undisputed king of the mobile phone market, has struggled to maintain its position in recent years.
Nokia, once the undisputed king of the mobile phone market, has struggled to maintain its position in recent years.
29. How the Domain Name System Works
30. How to Download a File Using cURL With Examples
 If you have ever used cURL to retrieve the output of a file, believe me, saving that output to a file only takes a few more characters.
If you have ever used cURL to retrieve the output of a file, believe me, saving that output to a file only takes a few more characters.
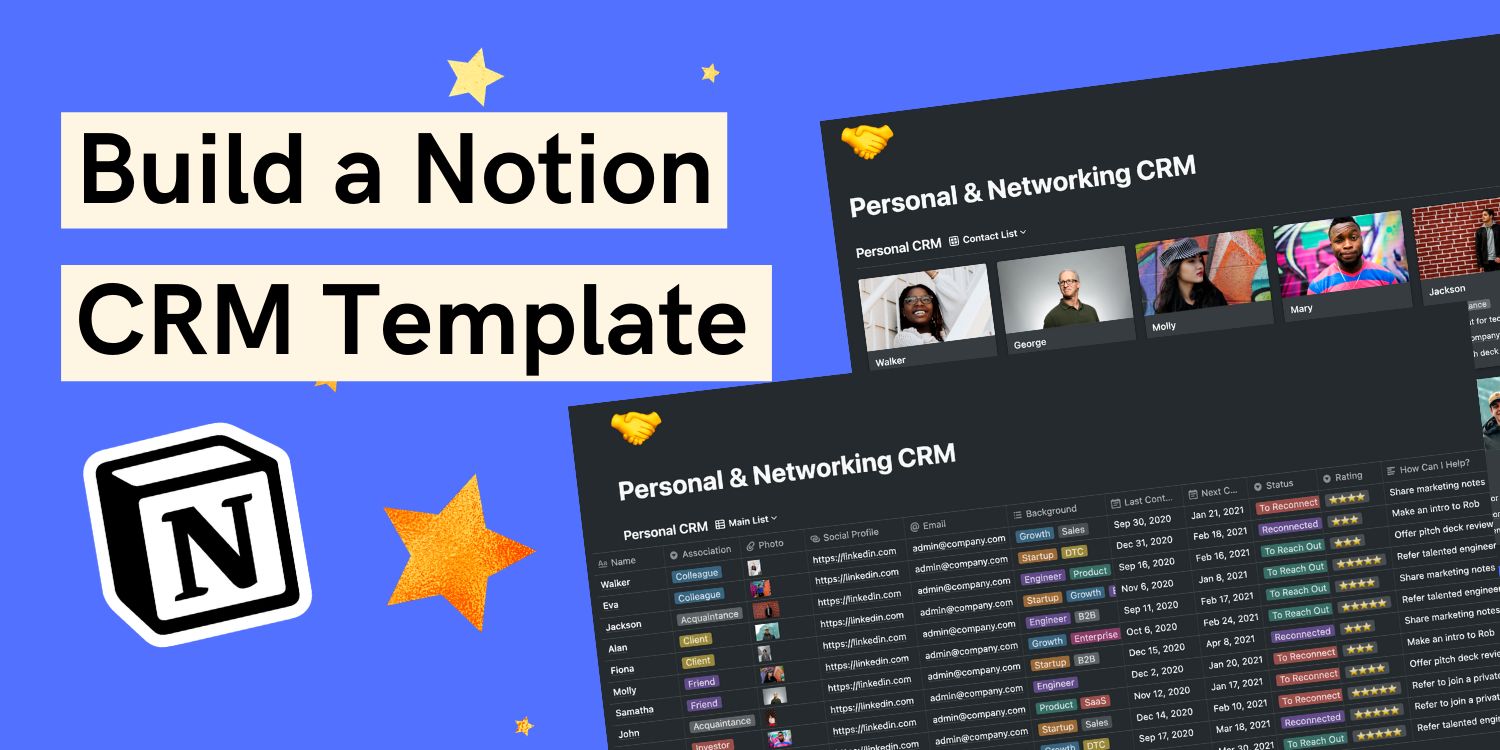
31. Notion CRM template: How I use it to Grow My Career
32. Ultimate Guide to LinkedIn: How to Harness the Professional Network
 LinkedIn is more than just a place to dump your resume and log out, and if you’re still using it that way you’re missing out on a lot of value. There are features rolling out all the time that few know even exist, let alone how to use to their advantage, and it’s time to take another look at this platform that is bringing business people together from all around the world in real, meaningful ways. If you’ve never used live and native video, document sharing, or attended a LinkedInLocal or Global Meetup for LinkedIn event, it’s time to take another look at just what LinkedIn can do for you.
LinkedIn is more than just a place to dump your resume and log out, and if you’re still using it that way you’re missing out on a lot of value. There are features rolling out all the time that few know even exist, let alone how to use to their advantage, and it’s time to take another look at this platform that is bringing business people together from all around the world in real, meaningful ways. If you’ve never used live and native video, document sharing, or attended a LinkedInLocal or Global Meetup for LinkedIn event, it’s time to take another look at just what LinkedIn can do for you.
33. Developing Cross-platform Qt Applications for BLE-based Systems
 Bluetooth Low Energy (BLE, Bluetooth LE, also known as Bluetooth Smart) is a form of wireless PAN technology that can be used to transfer data between devices.
Bluetooth Low Energy (BLE, Bluetooth LE, also known as Bluetooth Smart) is a form of wireless PAN technology that can be used to transfer data between devices.
34. An Introduction to AWS VPC
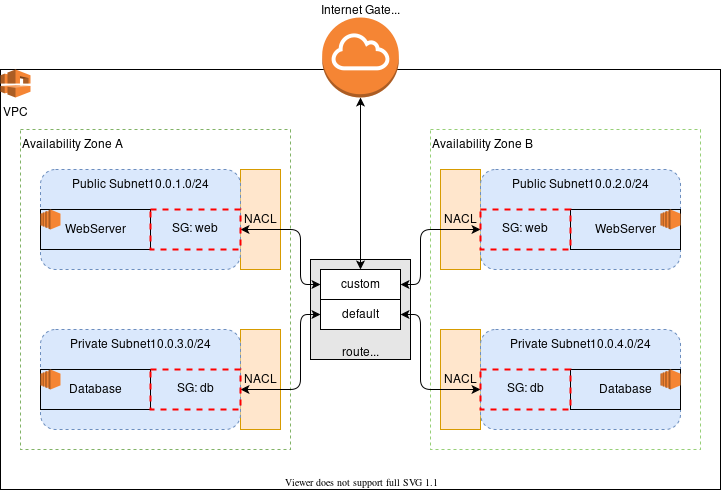 VPC is the topic that flies under the radar of many Software Developers, despite being present in every AWS account (well, maybe not for accounts created before 2009...but that's unlikely). There are a few reasons for this I can think of:
VPC is the topic that flies under the radar of many Software Developers, despite being present in every AWS account (well, maybe not for accounts created before 2009...but that's unlikely). There are a few reasons for this I can think of:
35. Going Beneath the GraphQL Federated API
 Want to understand how GraphQL Federation works? Follow on
Want to understand how GraphQL Federation works? Follow on
36. A Day in the Life of an SEO Consultant
 Working in the field of optimizing a website can mean a lot of things, but it’s definitely never boring! Here are some things that SEO Consultants do daily.
Working in the field of optimizing a website can mean a lot of things, but it’s definitely never boring! Here are some things that SEO Consultants do daily.
37. How do E-mails go From Your Computer to an Inbox
 Sending a message on Twitter is easy, Emails are not! Let's now see how emails reach an inbox.
Sending a message on Twitter is easy, Emails are not! Let's now see how emails reach an inbox.
38. Why Do Investors Say "No"?
 All startups hunt for capital, and in order to attract it from investors or funds they need, first of all, to contact them.
All startups hunt for capital, and in order to attract it from investors or funds they need, first of all, to contact them.
39. How to Be Careful When Sharing WiFi Password With QR Code
 Share your QR code of your network carefully, mistakes can lead to disaster
Share your QR code of your network carefully, mistakes can lead to disaster
40. Private Networks: How Tailscale Works
 People often ask us for an overview of how Tailscale works. We’ve been putting off answering that, because we kept changing it! But now things have started to settle down.
People often ask us for an overview of how Tailscale works. We’ve been putting off answering that, because we kept changing it! But now things have started to settle down.
41. 9 Things You Might Be Missing From Your Job Search Strategy
 A successful "Job Hunt" is a combination of Strategy, Marketing, and Sales tasks.
A successful "Job Hunt" is a combination of Strategy, Marketing, and Sales tasks.
42. "Stay hungry and go your own way", advised Felix Paul Wagner, Managing Partner of Next Mobility Lab
 Next Mobility Labs was nominated as one of the best startups in Mainz, Germany in Startups of the Year hosted by HackerNoon.
Next Mobility Labs was nominated as one of the best startups in Mainz, Germany in Startups of the Year hosted by HackerNoon.
43. Networking at VC Events: How to Gain More Value?
 The pandemic and lockdowns have proven to the world the simple truth that we are social beings.
The pandemic and lockdowns have proven to the world the simple truth that we are social beings.
44. What to do once you admit that decentralizing everything never seems to work
 Headquarters of the Internet Archive, home of the Decentralized Web conferences (Wikimedia Commons).
Headquarters of the Internet Archive, home of the Decentralized Web conferences (Wikimedia Commons).
45. Here Are 4 Easy Ways to Be Useful in Your Startup
 Life is not a race, but startups are. You have to add value to the market before the runway is up. Success and failure are binary.
Life is not a race, but startups are. You have to add value to the market before the runway is up. Success and failure are binary.
46. Attending Meetups: An Introvert's Guide
 If you've ever wondered why you should attend tech meetups, when you could simply stream them online, your concerns are valid.
If you've ever wondered why you should attend tech meetups, when you could simply stream them online, your concerns are valid.
47. Cisco Catalyst 3560-X Series Switches Features
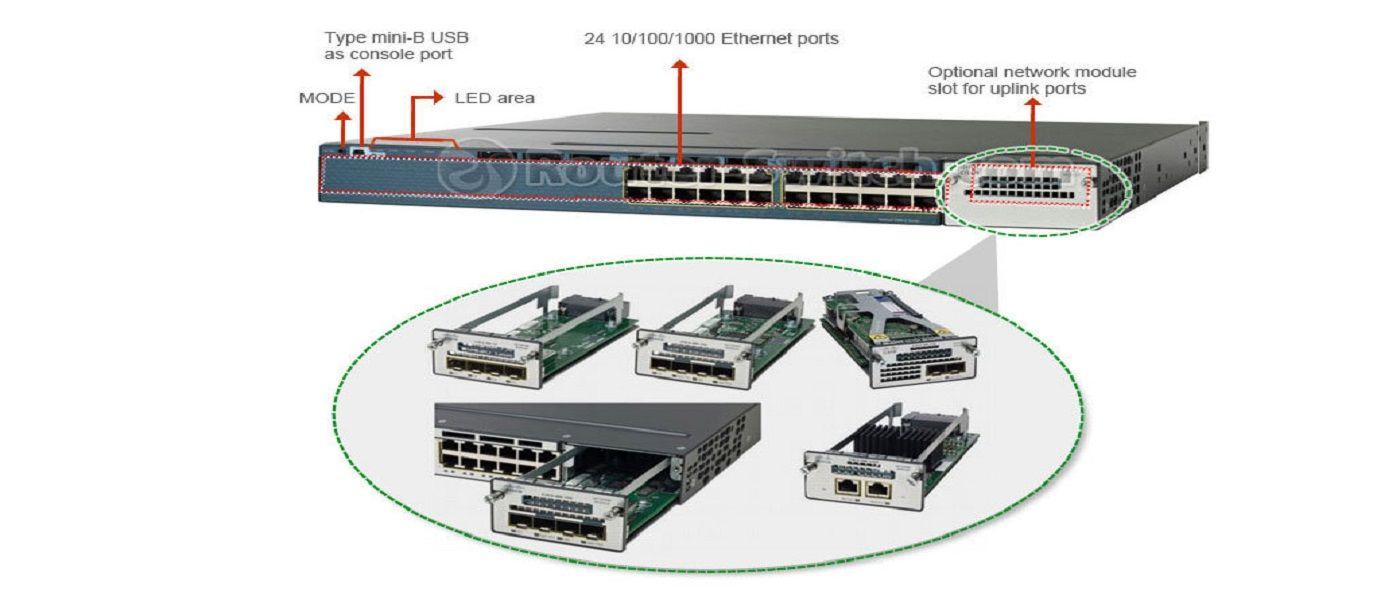 The Cisco Catalyst 3560-X Series Switches are business-class lines of stacking and standalone switches, respectively
The Cisco Catalyst 3560-X Series Switches are business-class lines of stacking and standalone switches, respectively
48. How to Host a Virtual Networking Event your Guests Will Never Forget
 In this article, you'll learn how you can use oVice virtual space to organize amazing events.
In this article, you'll learn how you can use oVice virtual space to organize amazing events.
49. Network Troubleshooting for the Well-Rounded Developer
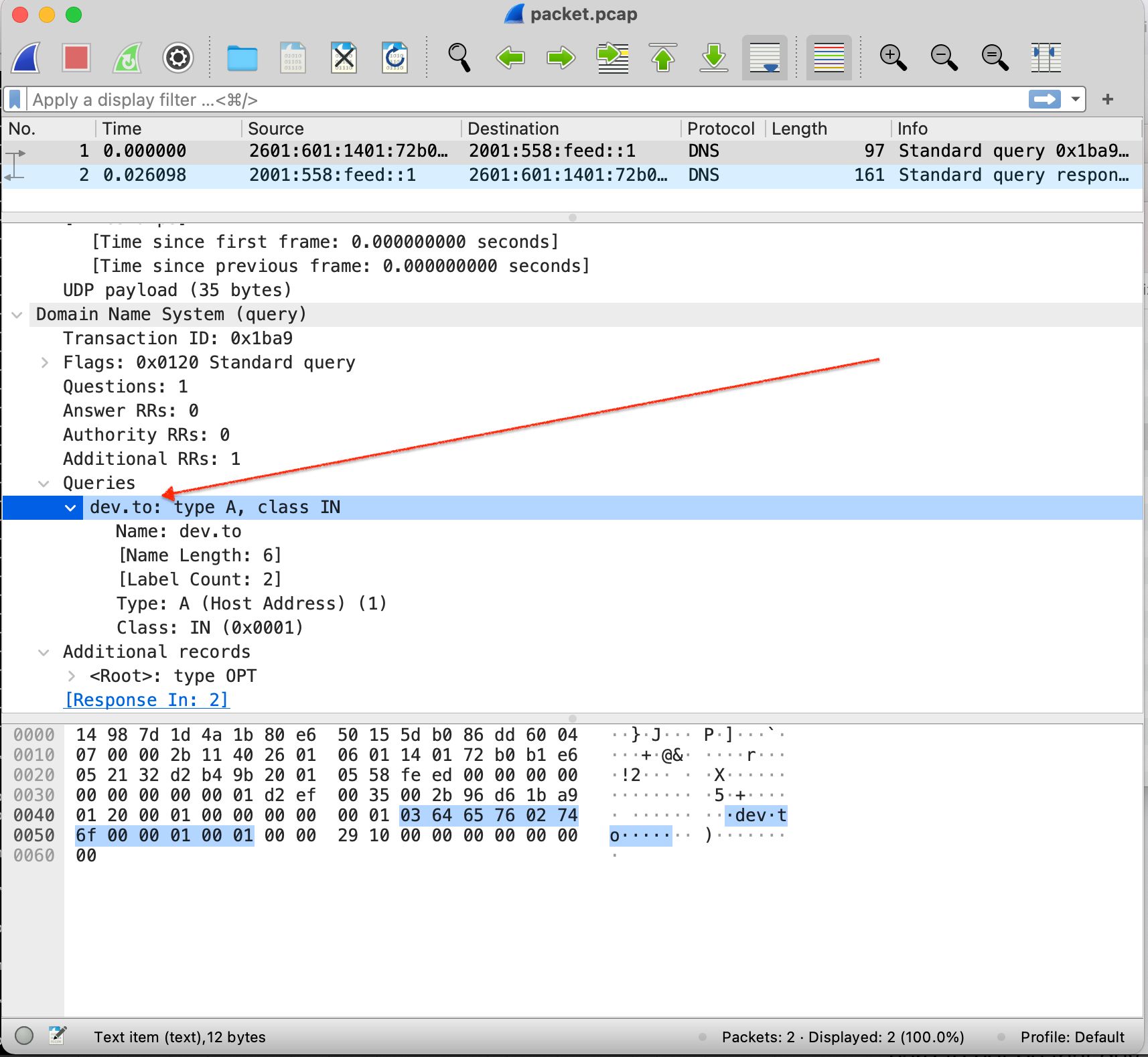 Regardless of whether you work on the front-end or back-end, I think all developers should gain some proficiency in network troubleshooting.
Regardless of whether you work on the front-end or back-end, I think all developers should gain some proficiency in network troubleshooting.
50. Don't Believe Everything About Agile

51. Proxy vs Reverse Proxy
 Proxy is an application or computer that mimics a user on the internet. Reverse proxy is the "REVERSE" of proxy that is used by server to route traffic.
Proxy is an application or computer that mimics a user on the internet. Reverse proxy is the "REVERSE" of proxy that is used by server to route traffic.
52. 6 Tips to Host a Successful Virtual Networking Event
 Here, we'll walk you through the 6 steps you can take to make your virtual event truly engaging and unique to your attendees.
Here, we'll walk you through the 6 steps you can take to make your virtual event truly engaging and unique to your attendees.
53. Get in Loser, We’re Going Networking!
 It seems like these days it’s all about operating in networks.
It seems like these days it’s all about operating in networks.
54. CGC|LIVE: Cutting-edge Games Conference Coming September 22 - 26
 Cutting-edge Games Conference invites all game industry professionals and enthusiasts to plunge into a completely different world for five days, to explore new capabilities of technology and creativity during the game developers’ conference sessions and on the online exhibition area!
Cutting-edge Games Conference invites all game industry professionals and enthusiasts to plunge into a completely different world for five days, to explore new capabilities of technology and creativity during the game developers’ conference sessions and on the online exhibition area!
55. A Guide to Network Gadgets that Contain Ping, NTP, TFTP, and Iperf
 In network-related product development and debugging, useful gadgets can often achieve more. Based on the network development scenario, RT-Thread developed the RT-Thread NetUtils component that collecting lots of easy-to-use network development tools for developers.
In network-related product development and debugging, useful gadgets can often achieve more. Based on the network development scenario, RT-Thread developed the RT-Thread NetUtils component that collecting lots of easy-to-use network development tools for developers.
56. A Single Speed Test is Fun — Hundreds of Them, May Actually be More Accurate
 Releasing the first internal build of the NordVPN apps that included NordLynx – our brand new protocol built on the backbone of WireGuard® – was an exciting moment for the team. Everyone started posting their speed test results on Slack and discussing the variance. While most of the time NordLynx outperformed other protocols, there were some cases with slightly worse speed results.
Releasing the first internal build of the NordVPN apps that included NordLynx – our brand new protocol built on the backbone of WireGuard® – was an exciting moment for the team. Everyone started posting their speed test results on Slack and discussing the variance. While most of the time NordLynx outperformed other protocols, there were some cases with slightly worse speed results.
57. How to Network Effectively and Enhance Your Career Growth
 This article is about why networking is important to your success, and what you can do to improve your networking skills throughout the course of your career.
This article is about why networking is important to your success, and what you can do to improve your networking skills throughout the course of your career.
58. Top Three Ways To Make Online Friends in the Digital Age of 2021
 It may feel overwhelming or demotivating that there are far fewer in-person opportunities to connect with new clients and associates than there used to be.
It may feel overwhelming or demotivating that there are far fewer in-person opportunities to connect with new clients and associates than there used to be.
59. Tips to Land a Job at a Top Tech Companies
 Landing a job at at Google, Apple and other similar companies in the world can seem like an impossible task. Read this guide you can land an interview in tech!
Landing a job at at Google, Apple and other similar companies in the world can seem like an impossible task. Read this guide you can land an interview in tech!
60. About the 5 Types of People You'll Meet at Virtual Networking Events
 The evolution of virtual meetings continues to break new ground.
The evolution of virtual meetings continues to break new ground.
61. How Certificate Chains Works
 Certificate chains are used to be able to verify an end user certificate against a list of intermediaries and a root authority. We are going to explain this in a bit more detail.
Certificate chains are used to be able to verify an end user certificate against a list of intermediaries and a root authority. We are going to explain this in a bit more detail.
62. How to Fix an Ethernet Cable Plug (RJ45 Plug) and Other Ethernet Tips
 Many of you have probably experienced problems with a broken RJ45 plug. The locking tab of RJ45 plugs breaks easily and this is one of the most common issues faced by the users of Ethernet cables. Now, I’ll tell you about a temporary solution that will help you make a connection with a broken plug more reliable.
Many of you have probably experienced problems with a broken RJ45 plug. The locking tab of RJ45 plugs breaks easily and this is one of the most common issues faced by the users of Ethernet cables. Now, I’ll tell you about a temporary solution that will help you make a connection with a broken plug more reliable.
63. Why The CCIE is My Favorite Intro Level Certification
 The CCIE certification has two other key benefits beyond opening the door to a deeper appreciation of the knowledge continuum in its area of expertise.
The CCIE certification has two other key benefits beyond opening the door to a deeper appreciation of the knowledge continuum in its area of expertise.
64. Network Marketing Tools You Must Use
 How to get the best network marketing tools? Here we discuss with you the best network marketing tools that will help you to manage your multi level marketing.
How to get the best network marketing tools? Here we discuss with you the best network marketing tools that will help you to manage your multi level marketing.
65. “I’m Too Small To Be Targeted,” Is No Longer A Valid Argument in 2021: A Database Security Checklist

66. A Look at the Power of Your Influence Network
 A look at the power of your influence network in college alumni and corporations.
A look at the power of your influence network in college alumni and corporations.
67. 19 things I learnt reading the NodeJSdocs
 I’d like to think I know Node pretty well. I haven’t written a web site that doesn’t use it for about 3 years now. But I’ve never actually sat down and read the docs.
I’d like to think I know Node pretty well. I haven’t written a web site that doesn’t use it for about 3 years now. But I’ve never actually sat down and read the docs.
68. 10 things InfoSec Professionals Need to Know About Networking

69. Rethinking Programming: Network-Aware Type System

70. Mums in Tech: Career and Family Need not Follow XOR (Exclusive OR) Logic
 Last Wednesday I’ve joined an event called Mums in Tech, how to balance work & family — Webinar + Virtual Networking, which was held by Women In Tech and hosted by Remo.
Last Wednesday I’ve joined an event called Mums in Tech, how to balance work & family — Webinar + Virtual Networking, which was held by Women In Tech and hosted by Remo.
71. Podcast Optimization and The Art of Networking: An Interview With Jordan Kastrinsky
 Today, Jordan talks about the ins and outs of starting a podcast channel, the key to reaching out for interviews, & the most promising marketing trends of 2023
Today, Jordan talks about the ins and outs of starting a podcast channel, the key to reaching out for interviews, & the most promising marketing trends of 2023
72. What is Software-Defined Networking and Why Is It the Future of Networking Connections?
 Software-defined networking, otherwise known as SDN, is a new approach to networking that has come to be favored by experienced technology professionals.
Software-defined networking, otherwise known as SDN, is a new approach to networking that has come to be favored by experienced technology professionals.
73. LinkedIn 101: What Social Media Managers Need to Know
 With 85% of the jobs found through networking, LinkedIn is at the heart of social media marketing, and LinkedIn 101 serves as a perfect guide for social media m
With 85% of the jobs found through networking, LinkedIn is at the heart of social media marketing, and LinkedIn 101 serves as a perfect guide for social media m
74. With Telehealth on the Rise, Privacy Regulations are Imperative
 In recent months, individuals across the globe have shifted to a remote way of life, including working from home, virtual dating, drive-by birthday parties and now, even doctor’s appointments. The healthcare sector quickly implemented changes to provide a more remote experience to comply with social distancing regulations.
In recent months, individuals across the globe have shifted to a remote way of life, including working from home, virtual dating, drive-by birthday parties and now, even doctor’s appointments. The healthcare sector quickly implemented changes to provide a more remote experience to comply with social distancing regulations.
To decrease the number of face-to-face doctor’s appointments and adhere to social distancing limitations and regulations, the Department of Health and Human Services (HHS) announced they “will not impose penalties for noncompliance” with the regulatory requirements under the HIPAA Rules against covered health care providers in connection with the good faith provision of telehealth during the COVID-19 nationwide public health emergency.
75. The Importance of Networking for Landing Remote Jobs

76. A Step By Step Guide To Becoming A Network Engineer
 Businesses are depending more than ever on networked devices to execute routine activities. As a result, they frequently require network engineers' assistance in the design, construction, setup, and maintenance of their computer networks. Learning how to start a network engineering profession might allow you to determine if this is the best path for you. In this post, we will cover what network engineering comprises and how to become a network engineer.
Businesses are depending more than ever on networked devices to execute routine activities. As a result, they frequently require network engineers' assistance in the design, construction, setup, and maintenance of their computer networks. Learning how to start a network engineering profession might allow you to determine if this is the best path for you. In this post, we will cover what network engineering comprises and how to become a network engineer.
77. What is CCNP Collaboration and How to Become a Cisco Professional?
 The CCNP Collaboration certification program prepares you for today's professional-level job roles in collaboration technologies.
The CCNP Collaboration certification program prepares you for today's professional-level job roles in collaboration technologies.
78. Network Security Basics
 Ever since the creation of the internet with all of the good that it has brought to the table came the bad as well. In the age of information technology, an unsecured product is a surefire way to numerous issues. A company, which creates a product has to make sure both the software and the network security features of it are as robust as possible. In the previous article we discussed application security, however, it is never complete without a clear network safeguards to serve as a frontline against malicious users trying to exploit the system. But what is network security and what are some of the methods used to protect systems?
Ever since the creation of the internet with all of the good that it has brought to the table came the bad as well. In the age of information technology, an unsecured product is a surefire way to numerous issues. A company, which creates a product has to make sure both the software and the network security features of it are as robust as possible. In the previous article we discussed application security, however, it is never complete without a clear network safeguards to serve as a frontline against malicious users trying to exploit the system. But what is network security and what are some of the methods used to protect systems?
79. Why Educational Platforms are a Favorite Target Among Attackers?
 Educational Institutes are easy prey for hackers to compromise and covertly launch Cyber Attacks/Malicious Campaigns under the hood, without divulging their real identity.
Educational Institutes are easy prey for hackers to compromise and covertly launch Cyber Attacks/Malicious Campaigns under the hood, without divulging their real identity.
[80. When We Can Pitch Startups at Events
Again, Take These Lessons With You](https://hackernoon.com/when-we-can-pitch-startups-at-events-again-take-these-lessons-with-you-in2jc3yio)
 Here I am, a twenty-year-old astrophysics student designing satellites to place in orbit around Mars and a self-starter entrepreneur longing to show my baby — nect MODEM — to the earth. I've had a few bumps on the road. Thankfully, I learned a few valuable lessons, and the experience of attending five conferences with my startup as my product made me reflect on a lot I'd like to share with other aspiring startup owners.
Here I am, a twenty-year-old astrophysics student designing satellites to place in orbit around Mars and a self-starter entrepreneur longing to show my baby — nect MODEM — to the earth. I've had a few bumps on the road. Thankfully, I learned a few valuable lessons, and the experience of attending five conferences with my startup as my product made me reflect on a lot I'd like to share with other aspiring startup owners.
81. Top 5 Business Tech Solutions For Networking
 Any business in the tech industry will know that an exceptional network is the backbone of any enterprise operation. Without a network that can adequately handle your internal operational demands, your business won’t be able to provide cutting-edge services to its customers.
Any business in the tech industry will know that an exceptional network is the backbone of any enterprise operation. Without a network that can adequately handle your internal operational demands, your business won’t be able to provide cutting-edge services to its customers.
82. Why do Modern Networks Require AIOps?
 With AIOps, you can start optimizing and managing your networks now and prepare for the future like never before. Read on.
With AIOps, you can start optimizing and managing your networks now and prepare for the future like never before. Read on.
83. BGP – What It Is and Why People are So Consumed with this Protocol
 The internet is huge. The number of active websites is approximately 200 million, with more than 250,000 new sites being added every day. The number of internet users is approximately 5 million. With that much activity, it takes a lot to send internet traffic to its destination. That is where BGP comes in.
The internet is huge. The number of active websites is approximately 200 million, with more than 250,000 new sites being added every day. The number of internet users is approximately 5 million. With that much activity, it takes a lot to send internet traffic to its destination. That is where BGP comes in.
84. Insights from Helping Devs at the Google Fest in Singapore
 Here's the theme for this week. This topic enlightens me as a perspective of someone who has never been to Developer related events, moreover even as facilitate a developer workshop (or study jam).
Here's the theme for this week. This topic enlightens me as a perspective of someone who has never been to Developer related events, moreover even as facilitate a developer workshop (or study jam).
85. How to Avoid Burning $80K+ on Tech Events: 10 Tips for Exhibiting Your Startup Efficiently
 Learn how to exhibit at startup events and tech conferences – and get the most out of your time and money!
Learn how to exhibit at startup events and tech conferences – and get the most out of your time and money!
86. Actionable Ways to Inspire Innovative Thinking in the Workplace
 Innovative thinking is a prowess that can be honed. Like everything else, it takes a little practice and some encouragement doesn’t hurt.
Innovative thinking is a prowess that can be honed. Like everything else, it takes a little practice and some encouragement doesn’t hurt.
87. 10 Best Practices for Using Kubernetes Network Policies
 In this article, we will explore 10 best practices for using Kubernetes Network Policies to enhance the security and reliability of your applications.
In this article, we will explore 10 best practices for using Kubernetes Network Policies to enhance the security and reliability of your applications.
88. The Complex Systems of Internet of Things Devices Explained
 The rise of IoT in networking is sparking key innovations in the field, including complex systems of Internet of Things devices (SIoTD). This guide will cover the basics of this emerging concept and its applications.
The rise of IoT in networking is sparking key innovations in the field, including complex systems of Internet of Things devices (SIoTD). This guide will cover the basics of this emerging concept and its applications.
89. How to Improve Network Security and Visibility in 2020 and 2021
 With the number of products available, it can be an uphill task to try to ensure robust network security and visibility. This, however, is a task that must be accomplished if you want to be competitive.
With the number of products available, it can be an uphill task to try to ensure robust network security and visibility. This, however, is a task that must be accomplished if you want to be competitive.
90. Code as Documentation and Assessment
 Documenting IT networking lab procedures in code rather than word-processor documents enables more authentic, equitable and consistent assessment.
Documenting IT networking lab procedures in code rather than word-processor documents enables more authentic, equitable and consistent assessment.
91. 5 Reasons to Get Published on HackerNoon
 Check out 5 reasons for aspiring writers and tech enthusiasts to get published on HackerNoon!
Check out 5 reasons for aspiring writers and tech enthusiasts to get published on HackerNoon!
92. 101 Small Business Marketing Ideas
 One universal small business goal is to sell the business's products and services. This is usually best accomplished by positioning the business in front of the target audience, and offering something that solves a problem or that they can't refuse or find elsewhere.
One universal small business goal is to sell the business's products and services. This is usually best accomplished by positioning the business in front of the target audience, and offering something that solves a problem or that they can't refuse or find elsewhere.
93. We Attended Web Summit. Here's a Rundown of How it Went Down
 Wait, do not close or flip the article just because it describes the experience of an IT service company. Actually, our experience may be useful for a working product company, early-stage startup, or anyone interested. If you are considering conferences as a new source of useful acquaintances and clients, then this article is what you need.
Wait, do not close or flip the article just because it describes the experience of an IT service company. Actually, our experience may be useful for a working product company, early-stage startup, or anyone interested. If you are considering conferences as a new source of useful acquaintances and clients, then this article is what you need.
Thank you for checking out the 93 most read stories about Networking on HackerNoon.
Visit the /Learn Repo to find the most read stories about any technology.

