Nearly two years have passed since the launch of the Proof of Scan** consensus protocol, which introduced a hybrid consensus model combining Proof of Work (PoW), utilizing recognition technology, and Proof of Authority (PoA). While the PoA component has progressed smoothly, the PoW aspect has faced ongoing challenges due to efforts to centralize the network through monopolistic mining practices.
To tackle this issue and achieve the high level of decentralization necessary for the 3DPRC-2** tokenization standard, the team has developed and released an upgraded PoW v2 component on The Ledger of Things mainnet. This new version is engineered to offer strong resistance against ASIC and FPGA mining devices.
In this article, we'll delve into the technical details of PoW v2, exploring its innovative features and explaining how it ensures a more distributed and equitable mining process across the network.
Key Differences Between PoW v1 and PoW v2 in Proof of Scan
Resistance to ASIC and FPGA Devices:
PoW v1: Originally vulnerable to specialized mining hardware like ASICs (Application-Specific Integrated Circuits) and FPGAs (Field-Programmable Gate Arrays), which could centralize mining efforts and control.
PoW v2: Designed with advanced algorithms to specifically resist ASIC and FPGA optimization, aiming to level the playing field for all participants and promote broader network decentralization.
Decentralization and Network Security:
PoW 1: Struggled with centralization issues as high-performance hardware could dominate the mining process, potentially leading to a concentration of power and reduced security.
PoW v2: Focuses on enhancing decentralization by making it harder for specialized hardware to gain a competitive edge, thus increasing overall network security and resilience against attacks.
Mining Accessibility:
PoW v1: Efficiency was often skewed towards those with access to high-end mining equipment, which could create barriers for average users.
PoW v2: Aims to improve accessibility by making mining more feasible for a wider range of participants, including those with standard consumer-grade hardware.
Algorithm and Technology Upgrades:
PoW v1: Utilized earlier algorithms which may have been less adaptive to evolving hardware technologies.
PoW v2: Implements more sophisticated and adaptive algorithms that continuously evolve to counteract advances in mining technology, ensuring ongoing fairness.
Economic Impact and Incentives:
PoW v1: The economic benefits were often disproportionately enjoyed by those who could afford the most advanced equipment.
PoW v2: Seeks to distribute mining rewards more equitably by diminishing the advantages of costly, specialized hardware, thus potentially increasing participation and overall network health.
Community Feedback and Adaptability:
PoW v1: Had limitations in its ability to quickly adapt to community feedback and emerging threats.
PoW v2: Incorporates community input and is designed with greater adaptability to address new challenges and opportunities as they arise.
This comprehensive update to the PoW system aims to address the centralization issues faced by its predecessor and enhance the overall robustness and fairness of the network.
Prohibiting the Reverse Method of Calculation
In many well-known Proof of Work (PoW) consensus protocols, the reverse method of nonce calculation is not typically an issue because the nonce itself is often just a few bytes in length. However, this changes dramatically when the nonce involves a complex 3D object shape, as is the case with 3DPass.
The Reverse Method:
The reverse method involves computing the block hash first and then deriving the 3D model from that hash. This approach is relatively straightforward and poses a potential exploit in systems like 3DPass. The process involves reversing the relationship between the nonce and the block hash, making it easier to reconstruct the nonce (in this case, the 3D model) from the hash rather than performing the more resource-intensive task of scanning random 3D objects.
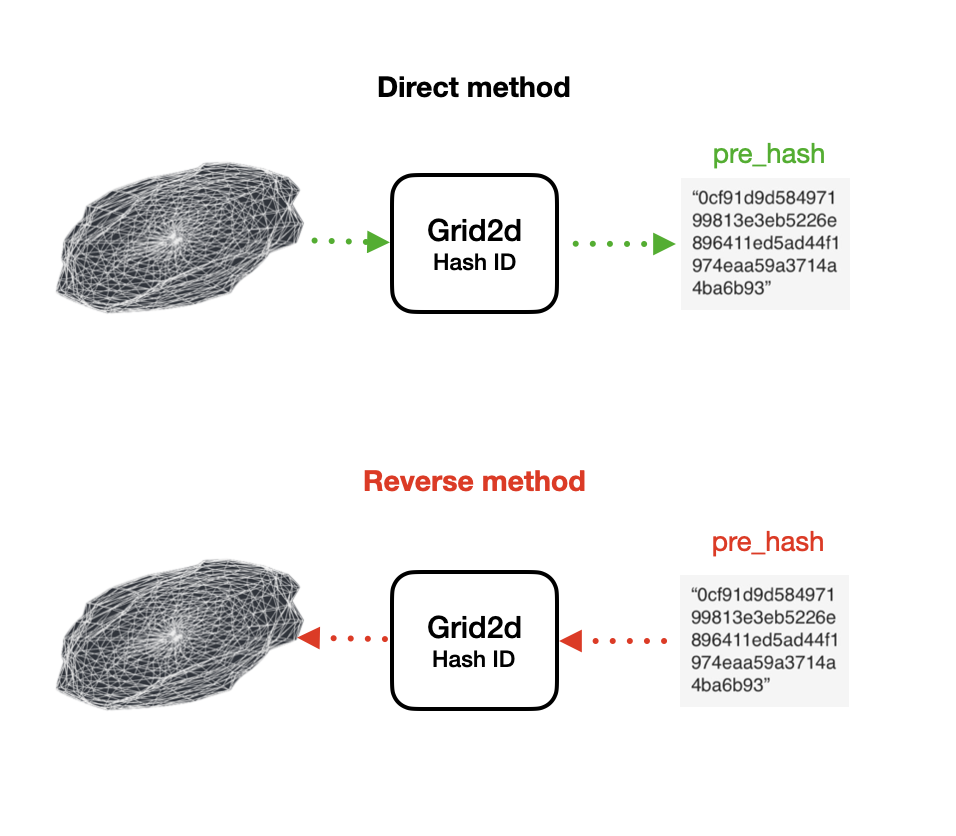
Addressing the Exploit:
To ensure the integrity of the PoW process and adhere to the strict requirements of handling user-submitted 3D objects through the 3DPRC-2 tokenization standard, this exploit needs to be effectively addressed. Prohibiting the reverse method of calculation ensures that all miners are required to engage in the genuine, computationally intensive process of scanning random 3D objects, thus maintaining a level playing field and promoting genuine decentralization.
By eliminating this shortcut, 3DPass aims to uphold the fairness and security of its mining process, ensuring that the system remains robust against potential manipulations and retains its intended decentralized nature.
Mining loop of PoW v2 in Proof of Scan:
- In order to prove 3D object exists at the beginning of the mining loop the bock author first must get random 3D object scanned with no rotation angle (μ = 0) resulting as Grid2d** output 1 (top 10 hashes). The second component is time_hash, which must timestamp upon the block header and impact the pre_hash (main block identifier), as well.
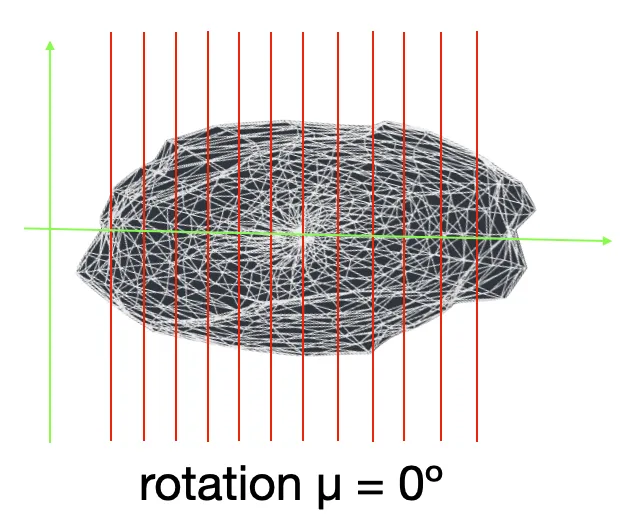
-
That is ensured by the rotation_bytes (by which the target rotation angle is defined) calculated out of a combination of both the pre_hash and the topest Grid2d zero-angled hash (μ = 0). So that any modification made on either of them will inevitably impact on the rest.
-
It wasn’t until having the object scanned with zero angle the target rotation angle (μ = x) could be calculated. The same as usual the block author would be challenged with picking up some 3D object shape and get it scanned with the target rotation angle (μ = x) until the pre_hash meets the current difficulty number.
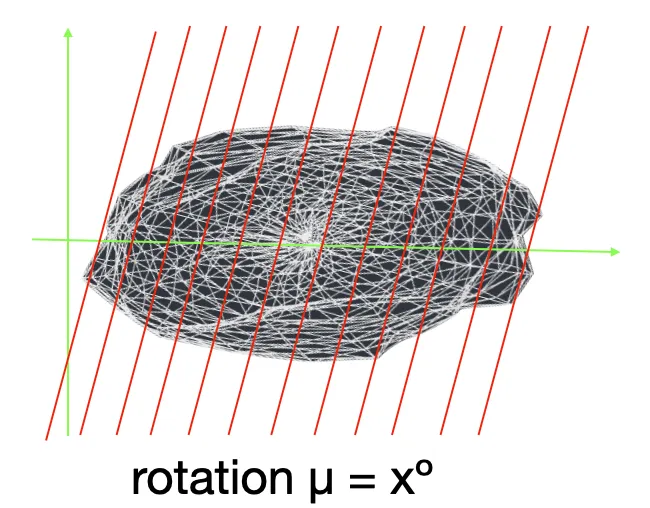
-
Both of the outputs of Grid2d μ = 0 and μ = x are getting processed by the RandomX** hashing algorithm to equalize CPU and GPU in terms of velocity of mining even further.
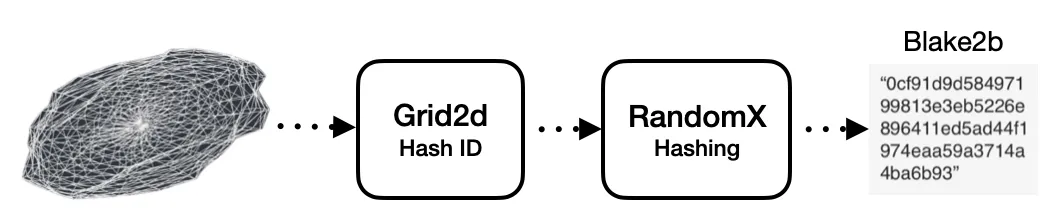
The entire cycle of the object processing would look like this:
Random 3D model in obj → Grid2d (3D model μ = 0) output → Random X (Grid2d μ = 0) blake2b hash → rotation_bytes x = 4 bytes out of pre_hash + 4 bytes out of RandomX (Grid2d μ = 0) blake2b hash → Grid2d (3D model μ = x) output → Random X (Grid2d μ = xo) blake2b hash
- There is a rule on new block import, which requires: Grid2d output 1 ≠ Grid2d output 2. Therefore, the object shape must be complex enough to entirely avoid the Grid2d recognition error that is most likely to face with, especially, when it comes to scanning some regular- shaped objects (ex. a sphere).
1 Node = 1 Vote rule
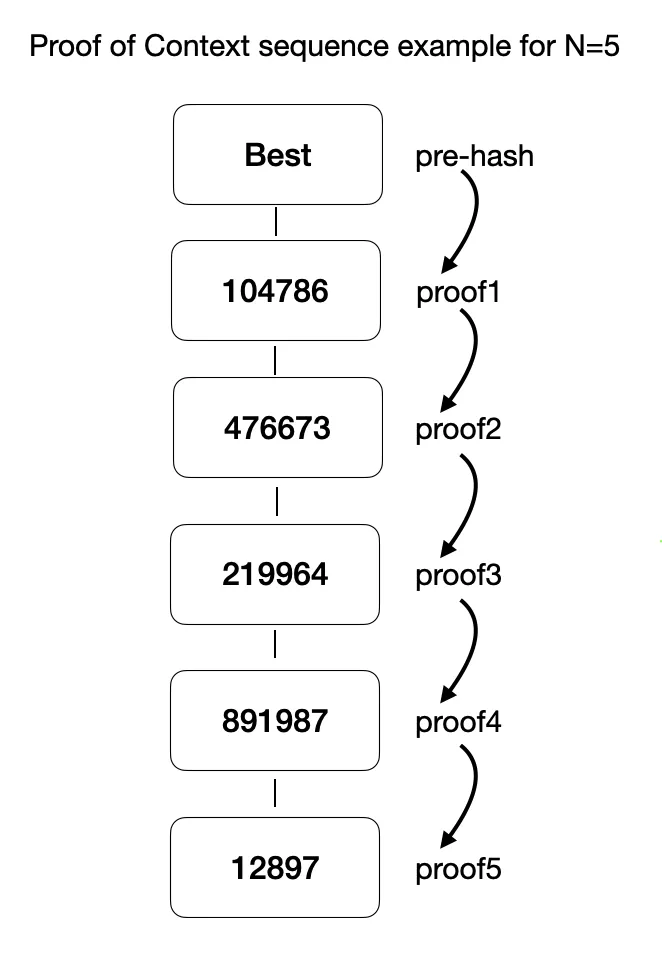
There will be an additional “proof of context” task to solve, having the access to the full blockchain db is required for. Depending on the pre_hash calculated, there is going to be a directed sequence of N pseudo randomly chosen blocks to pick up (ex. 104786 → 476673 → 219964 → 891987 → 12897) and prove its availability for the mining loop. Every mining loop will require another one different sequence to prove. The exact number of historical block steps required is being provided and managed by runtime.
Ensuring Direct Calculation and Responsibility
In the 3DPass system, the prohibition of the reverse method of calculation ensures that the block author is directly involved in both the calculation of the block and the processing of user-submitted 3D objects. Unlike traditional PoW protocols where nonce calculations might be simplified, the 3DPass model requires a more comprehensive approach.
Direct Calculation and Responsibility:
By eliminating the reverse calculation method, the responsibility for both block calculation and user object processing falls squarely on the block author. This means that the block author must perform the entire process of computing the block hash and handling the 3D objects from the user queue without outsourcing any part of the task to third parties.
Implications for Miners:
-
Ownership of Work: The block author is accountable for the complete mining process, including the verification and processing of user-submitted 3D objects. This ensures that every miner actively participates in the entire workflow, rather than relying on shortcuts or external resources.
-
Incentives and Penalties: Miners must handle and process user objects efficiently to avoid losing block rewards. If a block author fails to manage the user object queue, they risk forfeiting their rewards, reinforcing the need for active and responsible participation.
Ensuring Fairness:
This approach reinforces fairness and decentralization within the network. By mandating that each miner directly manages both the block calculation and the associated 3D object processing, 3DPass ensures that the mining process remains equitable and prevents exploitation of the system.
In summary, this method ensures that block authors are fully engaged in the mining process, maintaining the integrity and fairness of the 3DPass network while holding miners accountable for their role in both block creation and user object handling.
Reference**
- Proof of Scan consensus protocol: https://3dpass.org/proof-of-scan
- The implementation of The Ledger of Things Node: https://github.com/3Dpass/3DP
- 3Dpass White Paper v3: https://github.com/3Dpass/whitepaper/blob/main/3DPass_white_paper_v3.pdf
- Grid2d recognition algorithm description: https://3dpass.org/grid2d
- RandomX hashing https://github.com/tevador/RandomX/blob/master/doc/design.md
- 3DPRC-2 tokenizaton standard paper: https://github.com/3Dpass/whitepaper/blob/main/3DPRC-2.md
- The Ledger of Things mainnet distribution: https://www.3dpassmining.info
- Mining guidelines: https://3dpass.org/mainnet
Thank you!
Please keep this CTA when you submit:
Would you like to take a stab at answering some of these questions? The link for the template is