Let's learn about Cloud Security via these 69 free stories. They are ordered by most time reading created on HackerNoon. Visit the /Learn Repo to find the most read stories about any technology.
1. 9 Dropbox Alternatives for Evidence Management in Law Enforcement
 For evidence management and storage, there are multiple alternatives to Dropbox available which can save time and be customized for your specific needs.
For evidence management and storage, there are multiple alternatives to Dropbox available which can save time and be customized for your specific needs.
2. Cracking the SANS GSEC Certification
 The SANS GIAC Security Essentials (GSEC) certification is for anyone working in the field of Information Security.
The SANS GIAC Security Essentials (GSEC) certification is for anyone working in the field of Information Security.
3. Are AWS and GCP Actually 'Secure'?
 Cloud technologies are not a buzzword anymore. But there might be nuances. So, let’s take a look at security issues and how popular public clouds handle them.
Cloud technologies are not a buzzword anymore. But there might be nuances. So, let’s take a look at security issues and how popular public clouds handle them.
4. The Big Security Picture - A Case of Integrating CSPM into XDR
 Investing in both CSPM and XDR solutions allows organizations visibility into both the riskcape and the threatscape of their ecosystem.
Investing in both CSPM and XDR solutions allows organizations visibility into both the riskcape and the threatscape of their ecosystem.
5. Businesses Will Face These 4 Cloud Security Challenges in 2021
 As threats have sophisticated and evolved, new attacks emerge and it becomes more important than ever for businesses to embrace security first mentalities.
As threats have sophisticated and evolved, new attacks emerge and it becomes more important than ever for businesses to embrace security first mentalities.
6. How We Could Have Listened to Anyone’s Call Recordings
 How PingSafe managed to find and report a vulnerability in an automatic all recorder that would have allowed us to listen to anyone's call recordings
How PingSafe managed to find and report a vulnerability in an automatic all recorder that would have allowed us to listen to anyone's call recordings
7. 6 Data Cybersecurity Challenges with Cloud Computing
 It is important to keep your data safe and secure. Here are six challenges in that hosting your data on the cloud can pose and how your data security can help.
It is important to keep your data safe and secure. Here are six challenges in that hosting your data on the cloud can pose and how your data security can help.
8. What Makes a Cloud Enterprise Technology Stand Out
 This article covers the top eight factors you should consider when choosing a cloud enterprise technology.
This article covers the top eight factors you should consider when choosing a cloud enterprise technology.
9. Linux Ransomware, Cryptojacking, and Cobalt Strike Are Targeting Multi-Cloud Infrastructure
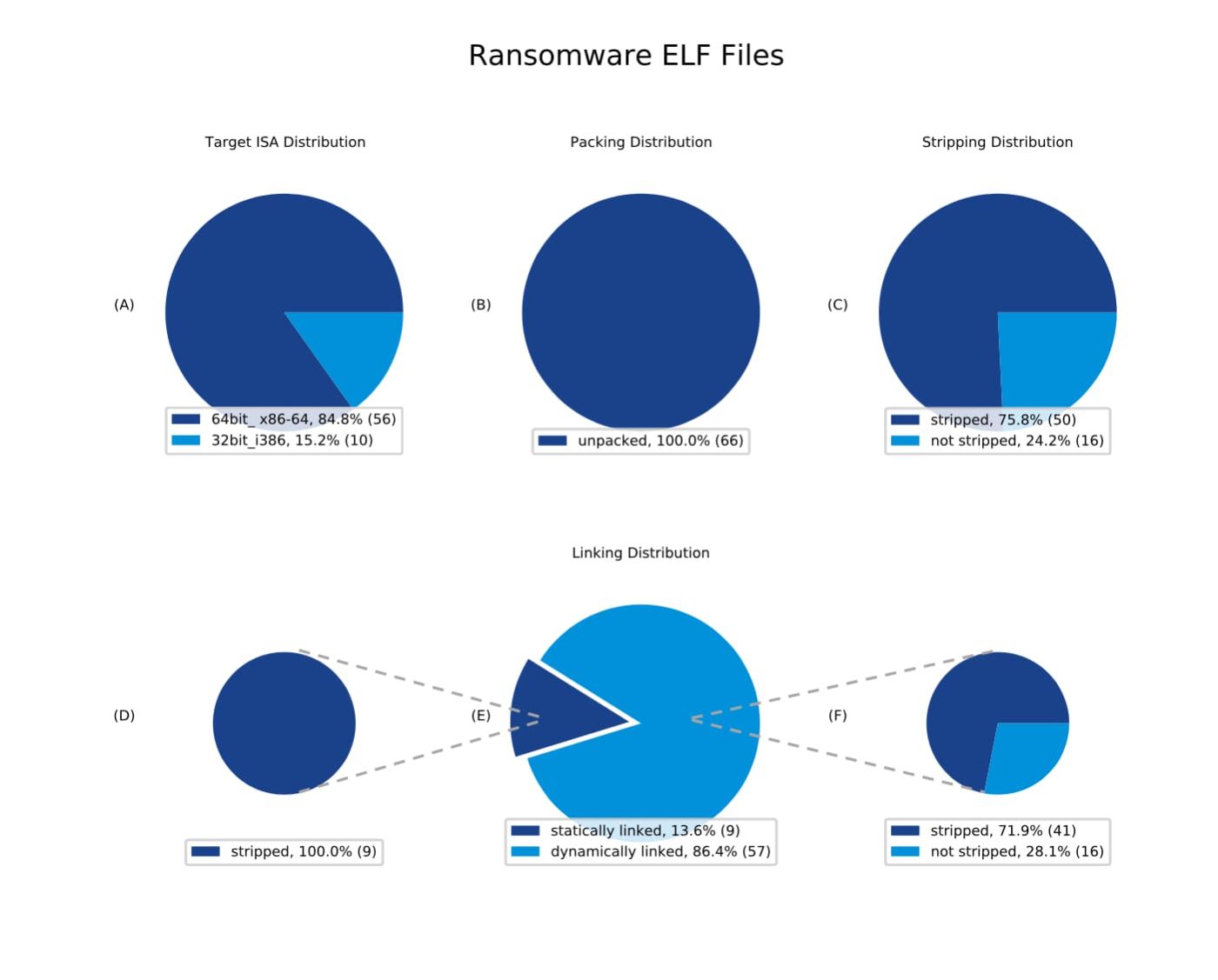 Linux systems are being increasingly targeted by ransomware, cryptojacking, and other malicious attacks, according to a recent report.
Linux systems are being increasingly targeted by ransomware, cryptojacking, and other malicious attacks, according to a recent report.
10. Check Your Privilege: Designing Cloud Infrastructures According to the Least Privilege Principle
 The Sunburst attacks relied on the Cloud model to work successfully. Experts believe that Dark Halo, the group responsible, used priviledges to do it.
The Sunburst attacks relied on the Cloud model to work successfully. Experts believe that Dark Halo, the group responsible, used priviledges to do it.
11. Power E1080: A Poem
 Turn your inverted camera thirty degrees to the mobius strip shape on the right and record
Turn your inverted camera thirty degrees to the mobius strip shape on the right and record
12. Is Cloud Computing Really More Sustainable?
 We've all heard the environmental benefits of cloud computing, but there are some cons as well. Is the cloud really more sustainable?
We've all heard the environmental benefits of cloud computing, but there are some cons as well. Is the cloud really more sustainable?
13. My AWS Cloud Resume Challenge Journey (Part One)
 I intend to take my readers on a journey of skills learned, challenges faced, and solutions uncovered along the way as I take on the cloud resume AWS challenge.
I intend to take my readers on a journey of skills learned, challenges faced, and solutions uncovered along the way as I take on the cloud resume AWS challenge.
14. Cloud Security Observability: Get Set, Go!
 The cloud security observability approach involves applying the observability concepts to cloud security operations to gain insights into the health of an app.
The cloud security observability approach involves applying the observability concepts to cloud security operations to gain insights into the health of an app.
15. Managing Enterprise Cloud Security vs On-Prem Security
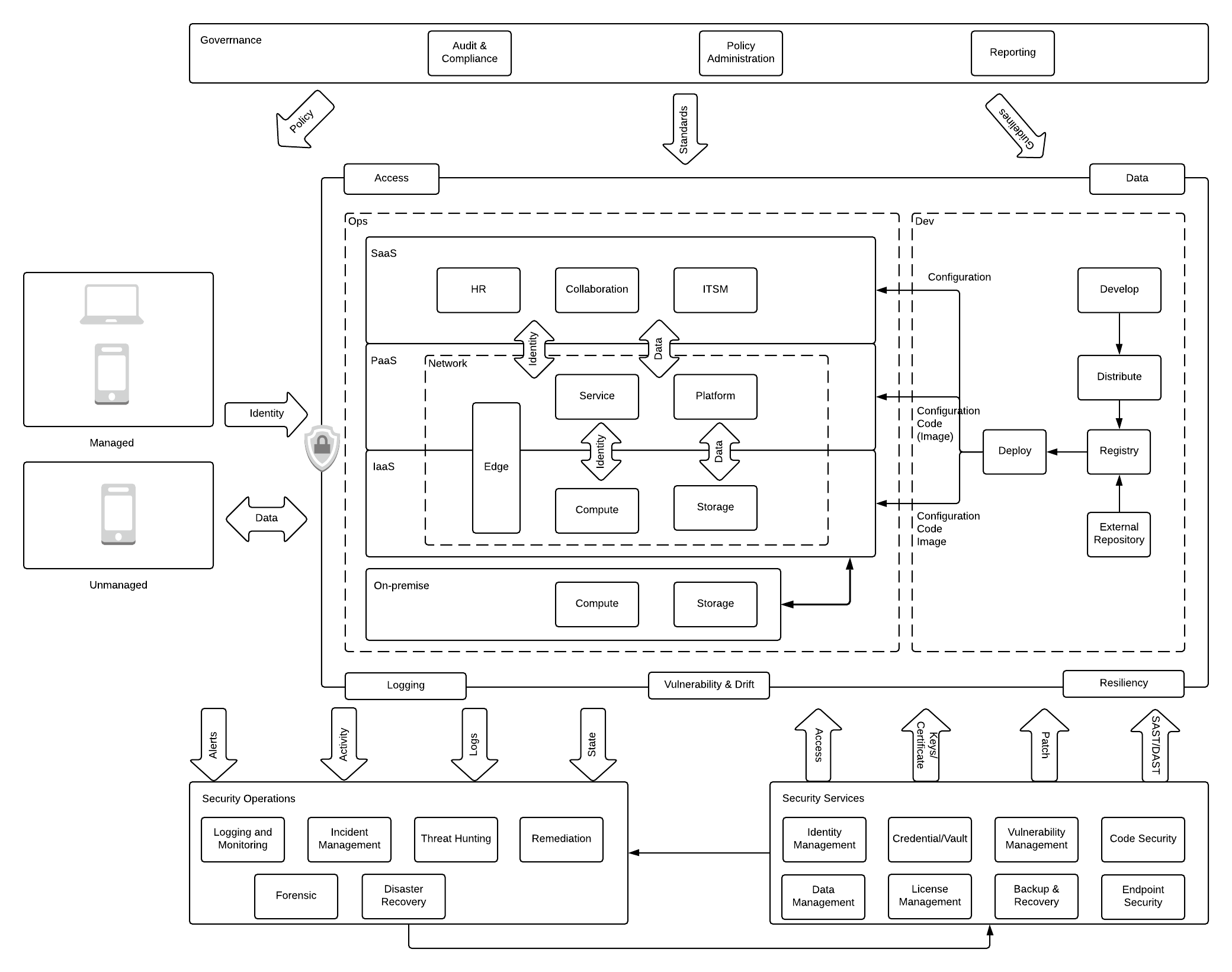
16. Viewing K8S Cluster Security from the Perspective of Attackers (Part 1)
 Based on previous penetration testing experience, we have sorted out the possible security issues under the K8S cluster architecture.
Based on previous penetration testing experience, we have sorted out the possible security issues under the K8S cluster architecture.
17. Cybersecurity in Times of International Conflicts: How to Protect Your Organization
 On June 28, the Baton Rouge General Medical Center in Louisiana lost its electronic medical record and patient system to a cyberattack
On June 28, the Baton Rouge General Medical Center in Louisiana lost its electronic medical record and patient system to a cyberattack
18. How to Master AWS Identity and Access Management
 From the basic to advanced concepts of AWS own service for identity and access management: users, groups, permissions for resources and much more.
From the basic to advanced concepts of AWS own service for identity and access management: users, groups, permissions for resources and much more.
19. Don’t Fear The Cloud When it Comes to Data Integration
 Data loading speed, cloud applications, data security fears, and added costs & efforts are some of the reasons why businesses fear data integration.
Data loading speed, cloud applications, data security fears, and added costs & efforts are some of the reasons why businesses fear data integration.
20. The 4 Biggest Cloud Computing Security Challenges
 Before adopting a range of cloud services and apps, there are a few cloud computing security issues and challenges you need to address. Learn more here.
Before adopting a range of cloud services and apps, there are a few cloud computing security issues and challenges you need to address. Learn more here.
21. What Does the Future Hold for Cloud Security?
 Cloud security is something that every business needs to take seriously. In fact, ignoring cloud security could prove to be a fatal move for many organizations.
Cloud security is something that every business needs to take seriously. In fact, ignoring cloud security could prove to be a fatal move for many organizations.
22. Why your Company Needs a Virtual Chief Information Security Officer
 Why should your company hire a virtual CISO to increase security?
Why should your company hire a virtual CISO to increase security?
23. 5 Types of Cyber Security and Why It’s Important to be Aware of Them
 Cybersecurity is the process of protecting systems, networks, and programs from malicious attacks. But why is it important? Let’s find out.
Cybersecurity is the process of protecting systems, networks, and programs from malicious attacks. But why is it important? Let’s find out.
24. 9 Information Technology Industry Trends for 2023

25. Why You Should Use IAM Policies to Enforce MFA on AWS
 In my past life, I was an auditor and performed hundreds of cybersecurity
readiness assessments. These were sometimes called “gap analysis” and
the essential purpose of these assessments were to provide organizations with the answers to the test for their upcoming official assessment.
In my past life, I was an auditor and performed hundreds of cybersecurity
readiness assessments. These were sometimes called “gap analysis” and
the essential purpose of these assessments were to provide organizations with the answers to the test for their upcoming official assessment.
26. How to Tell If Someone Hacked Your Active Directory
 The latest cybersecurity reports show that more breaches in the current day are done through credential leaks done through an active directory compromise
The latest cybersecurity reports show that more breaches in the current day are done through credential leaks done through an active directory compromise
27. Securing Serverless Applications with Critical Logging
 Serverless security: How important are logs to secure a serverless app? Here's what and how to log based on the industry best practices.
Serverless security: How important are logs to secure a serverless app? Here's what and how to log based on the industry best practices.
28. AI Will Reshape the Cybersecurity World in 2021
 Cybersecurity providers will step up AI development to merge human and machine understanding to outpace cybercriminals' goal of staging an arms race.
Cybersecurity providers will step up AI development to merge human and machine understanding to outpace cybercriminals' goal of staging an arms race.
29. 3 Methods to Secure Your AWS Cloud Infrastructure
 79% of surveyed firms have recently experienced a cloud data breach. In this article, we examined various recommended practices that can help you stay safe.
79% of surveyed firms have recently experienced a cloud data breach. In this article, we examined various recommended practices that can help you stay safe.
30. Cloud Complexity Causes Security Headaches - Can Identity Cure It?
 As the cloud industry grew by leaps and bounds, it has become more compex, making it harder to keep data safe from hackers. Can Identity Management help?
As the cloud industry grew by leaps and bounds, it has become more compex, making it harder to keep data safe from hackers. Can Identity Management help?
31. Why Vulnerability Detection is Important in the IT Space
 A look at why vulnerability detection is important in the it space
A look at why vulnerability detection is important in the it space
32. What's Stopping Everyone From Going Serverless?
 In this article, we'll look at what are the security hazards in serverless and what factors will drive its development in the following years.
In this article, we'll look at what are the security hazards in serverless and what factors will drive its development in the following years.
33. Top 3 Multi-Cloud Management Challenges and Solutions
 Multi-cloud solutions are on the rise & face many challenges. This piece discusses the top-3 multi-cloud challenges and proposed solutions for each challenge.
Multi-cloud solutions are on the rise & face many challenges. This piece discusses the top-3 multi-cloud challenges and proposed solutions for each challenge.
34. Kubernetes Security 101: Cloud Native Runtime Security with Falco
 As Kubernetes continues to grow in adoption, it is important for us to know how to secure it. In a dynamic infrastructure platform such as Kubernetes
As Kubernetes continues to grow in adoption, it is important for us to know how to secure it. In a dynamic infrastructure platform such as Kubernetes
35. What Poses a Challenge to Security in a Multi-Cloud Environment
 Multi-cloud gives you much more flexibility because it allows you to find the perfect solution for each of your business requirements.
Multi-cloud gives you much more flexibility because it allows you to find the perfect solution for each of your business requirements.
36. Research: The Misconfiguration of Real Time Databases in Mobile App Development
 Mobile App Development is a hugely useful tool but it does come with significant security risks, as the Checkpoint found out when researching threats.
Mobile App Development is a hugely useful tool but it does come with significant security risks, as the Checkpoint found out when researching threats.
37. How a Unified Approach to Cloud Data Security Can Come To Your Aid
 A unified approach to clould data security has significant advantages to cybersecurity relative to conventional methods of cybersecurity and may be helpful.
A unified approach to clould data security has significant advantages to cybersecurity relative to conventional methods of cybersecurity and may be helpful.
38. How to Revolutionize Data Security Through Homomorphic Encryption
 For decades, we have benefited from modern cryptography to protect our sensitive data during transmission and storage. However, we have never been able to keep the data protected while it is being processed.
For decades, we have benefited from modern cryptography to protect our sensitive data during transmission and storage. However, we have never been able to keep the data protected while it is being processed.
39. Cloud Threat Hunting Series: What Lead To a Major Financial Institution Suffering a Cloud Breach
 Even the greatest cybersecurity arrangements can be vunerable to simple mistakes such as a tiny setting being misconfigured, compromising the entire system.
Even the greatest cybersecurity arrangements can be vunerable to simple mistakes such as a tiny setting being misconfigured, compromising the entire system.
40. How to Maximize Cloud ROI With Containerization - Part 1
 Struggling to make the most of cloud-hosted applications? Learn about containerization, its optimization challenges, and potential solutions.
Struggling to make the most of cloud-hosted applications? Learn about containerization, its optimization challenges, and potential solutions.
41. Why You Should Think About Switching To The Cloud Hosting today
 Cloud computing has become essential for most homes and businesses, and it has been critical in reducing social upheaval and economic devastation.
Cloud computing has become essential for most homes and businesses, and it has been critical in reducing social upheaval and economic devastation.
42. Enterprise Cloud Security Guide: Secure Application Development
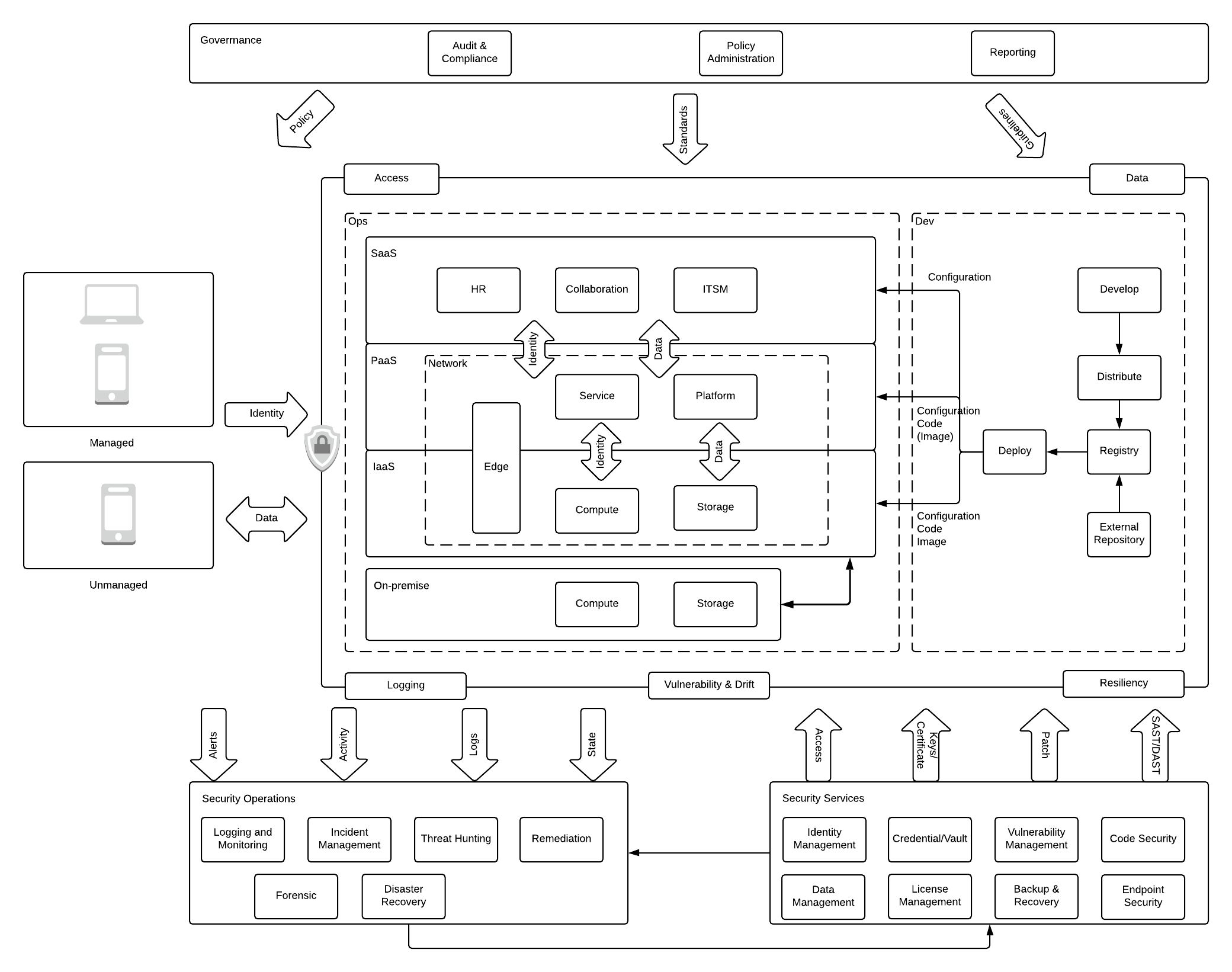 This article focuses on DevSecOps and explores how to secure applications during DevOps and the security of the platform itself.
This article focuses on DevSecOps and explores how to secure applications during DevOps and the security of the platform itself.
43. I Have My Own AWS VPC, and Now You Can Too!
 Let's see how a default VPC is configured in AWS, CIDR block, the associated subnets within it, routes, NACLs and Security Groups.
Let's see how a default VPC is configured in AWS, CIDR block, the associated subnets within it, routes, NACLs and Security Groups.
44. Cyber-Resilience On the Cloud by Adopting Digital Immune System and CNAPP
 This blog post will analyze the similarities and differences between CNAPP, DIS, and Cyber Resilience.
This blog post will analyze the similarities and differences between CNAPP, DIS, and Cyber Resilience.
45. The Emergence of IoT Security in The Post-COVID-19 World
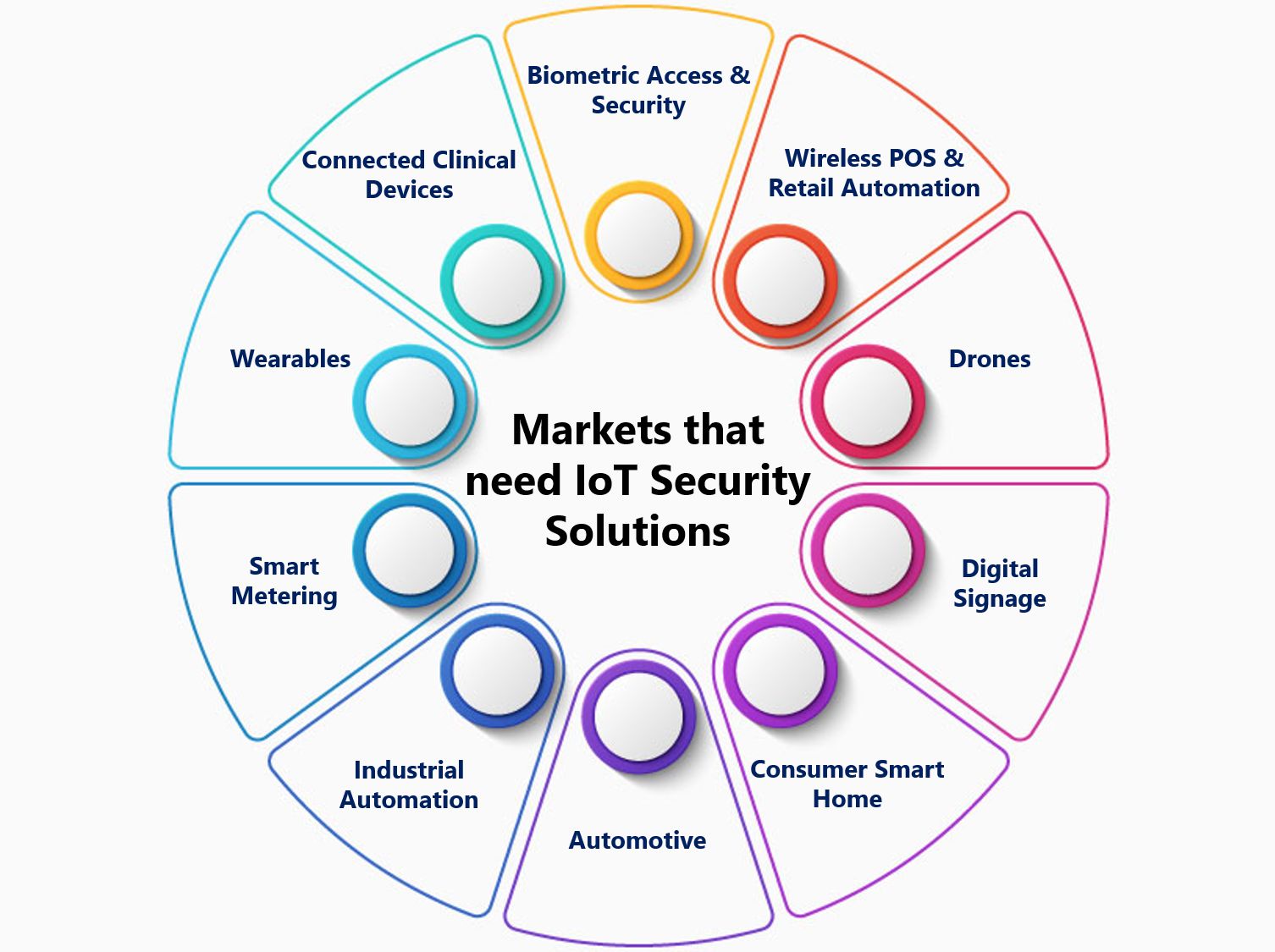 Security is a ‘state of mind’ and not an end state. It has been a popular philosophical thought, but what it eludes is the fact of investment towards security. IoT has exploded with the onset of new smart tech gadgets. Though businesses today exercise security and safety measures within their organizations, it isn’t easy to keep upgrading an organization’s infrastructure to encompass these technology updates. Reverse engineering systems have always remained the passcode for unlocking backdoors to capitalize on security vulnerabilities. The best example of such a scenario is the 2016 MIRAI botnet attack. The attack caused massive DDoS attacks on large enterprises on Atlanta’s city administration and the ATL airport. IoT still lacks immunity against ransomware attacks and many new age cyberattacks.
Security is a ‘state of mind’ and not an end state. It has been a popular philosophical thought, but what it eludes is the fact of investment towards security. IoT has exploded with the onset of new smart tech gadgets. Though businesses today exercise security and safety measures within their organizations, it isn’t easy to keep upgrading an organization’s infrastructure to encompass these technology updates. Reverse engineering systems have always remained the passcode for unlocking backdoors to capitalize on security vulnerabilities. The best example of such a scenario is the 2016 MIRAI botnet attack. The attack caused massive DDoS attacks on large enterprises on Atlanta’s city administration and the ATL airport. IoT still lacks immunity against ransomware attacks and many new age cyberattacks.
46. Hundreds of Google and Amazon Employees Oppose the Israeli "Nimbus" Cloud Project
 Hundreds of Google and Amazon employees anonymously sign a letter opposing the tech giants’ deal with Israel.
Hundreds of Google and Amazon employees anonymously sign a letter opposing the tech giants’ deal with Israel.
47. Your Ultimate Guide To The 4 Types of IT Security
 IT Security protects your business against cyber threats. There are four types of IT Security: network security, end-point security, internet & cloud security.
IT Security protects your business against cyber threats. There are four types of IT Security: network security, end-point security, internet & cloud security.
48. Cloud Security Strategies For Small Businesses
 If you work from home and use cloud solutions to archive business documents, who is responsible for Cloud Security
If you work from home and use cloud solutions to archive business documents, who is responsible for Cloud Security
49. Cloud Security: Is it Worth it?
 Storing and managing corporate data by applying the cloud is becoming more and more popular. Companies grow, and it gets too expensive, and resources consuming to store their data on traditional servers. To prove it, look at the research conducted by Google in 2019 that includes insights for the cloud computing market for the next 10 years.
Storing and managing corporate data by applying the cloud is becoming more and more popular. Companies grow, and it gets too expensive, and resources consuming to store their data on traditional servers. To prove it, look at the research conducted by Google in 2019 that includes insights for the cloud computing market for the next 10 years.
50. CVEs: How Keeping a Catalogue of Common Vulnerabilities and Exposures Helps Your Company
 CVE combines a dictionary and a catalog containing names for vulnerabilities and other information security vulnerabilities.
CVE combines a dictionary and a catalog containing names for vulnerabilities and other information security vulnerabilities.
51. It's Raining Cyber Attacks: Cybersecurity in the Cloud
 With the latest news and advancements in the cybersecurity world, we will see how these new rules impact modern cloud applications.
With the latest news and advancements in the cybersecurity world, we will see how these new rules impact modern cloud applications.
52. Essential Aspects of Cloud Compliance for Financial Services
 In this post, we will cover five key areas that are very relevant to most financial services businesses—five topics an organization must “get right”.
In this post, we will cover five key areas that are very relevant to most financial services businesses—five topics an organization must “get right”.
53. Security Infrastructure and the Multi-Cloud
 Achieving high-availability cloud architecture requires more than one cloud. From an architecture perspective, there are only three options for mission critical
Achieving high-availability cloud architecture requires more than one cloud. From an architecture perspective, there are only three options for mission critical
54. What Makes Cloud Security Solutions so Relevant
 Intuitively, some people believe that “cloud” storage means your data is being held in the air somehow, but this isn’t really the case.
Intuitively, some people believe that “cloud” storage means your data is being held in the air somehow, but this isn’t really the case.
55. How To Eliminate Leaky S3 Buckets Without Writing A Line Of Code
 FedEx
FedEx
56. AWS re:Invent 2020: AWS Community Builders Program Top Highlights
 As an AWS Community Builder, I truly enjoyed attending AWS' re:Invent 2020 conference this year, diving into cloud technology, devops, databases & innovation.
As an AWS Community Builder, I truly enjoyed attending AWS' re:Invent 2020 conference this year, diving into cloud technology, devops, databases & innovation.
57. Top 5 Reasons Why Companies are Moving to the Cloud
 Cloud has introduced some new business capabilities through cost-effectiveness or accessibility, as a company you don't want to miss the opportunity.
Cloud has introduced some new business capabilities through cost-effectiveness or accessibility, as a company you don't want to miss the opportunity.
58. Cloud Security 101
 Cloud security involves the procedures and technology that secure cloud computing environments against external and insider cybersecurity threats.
Cloud security involves the procedures and technology that secure cloud computing environments against external and insider cybersecurity threats.
59. What the Heck Is Envelope Encryption in Cloud Security?
 If you are going deep into cloud security you may have seen the term “Envelope encryption”. Let’s explain the concept and why it is useful.
If you are going deep into cloud security you may have seen the term “Envelope encryption”. Let’s explain the concept and why it is useful.
60. Application Security Posture Management: An Overview
 Application Security Posture Management (ASPM) is a holistic approach to managing the security posture of applications throughout their lifecycle.
Application Security Posture Management (ASPM) is a holistic approach to managing the security posture of applications throughout their lifecycle.
61. Crucial Cloud Computing Security Threats Everyone Should Know
 A rundown of the business impact and mitigation measures of the top cloud computing security threats from the 2022 Cloud Security Alliance survey
A rundown of the business impact and mitigation measures of the top cloud computing security threats from the 2022 Cloud Security Alliance survey
62. Can Blockchain Fix Enterprise Cloud Computing?
 As cloud waste increases, businesses are looking for a silver lining.
As cloud waste increases, businesses are looking for a silver lining.
63. Cloud Threat Hunting: Investigating Lateral Movement
 What is the most involved attack flow yet? We will break down all of the steps a threat actor took to successfully exfiltrate data out of an AWS account.
What is the most involved attack flow yet? We will break down all of the steps a threat actor took to successfully exfiltrate data out of an AWS account.
64. 6 Cloud Predictions for the Near Future

65. Strategies for Combating Cloud Security Risks
 There are some proven operational and security practices to significantly reduce the occurrence and impact of security breaches in the cloud.
There are some proven operational and security practices to significantly reduce the occurrence and impact of security breaches in the cloud.
66. Enterprise Cloud Security: Setting Up Structure, Identity-Based Access, and Network Control
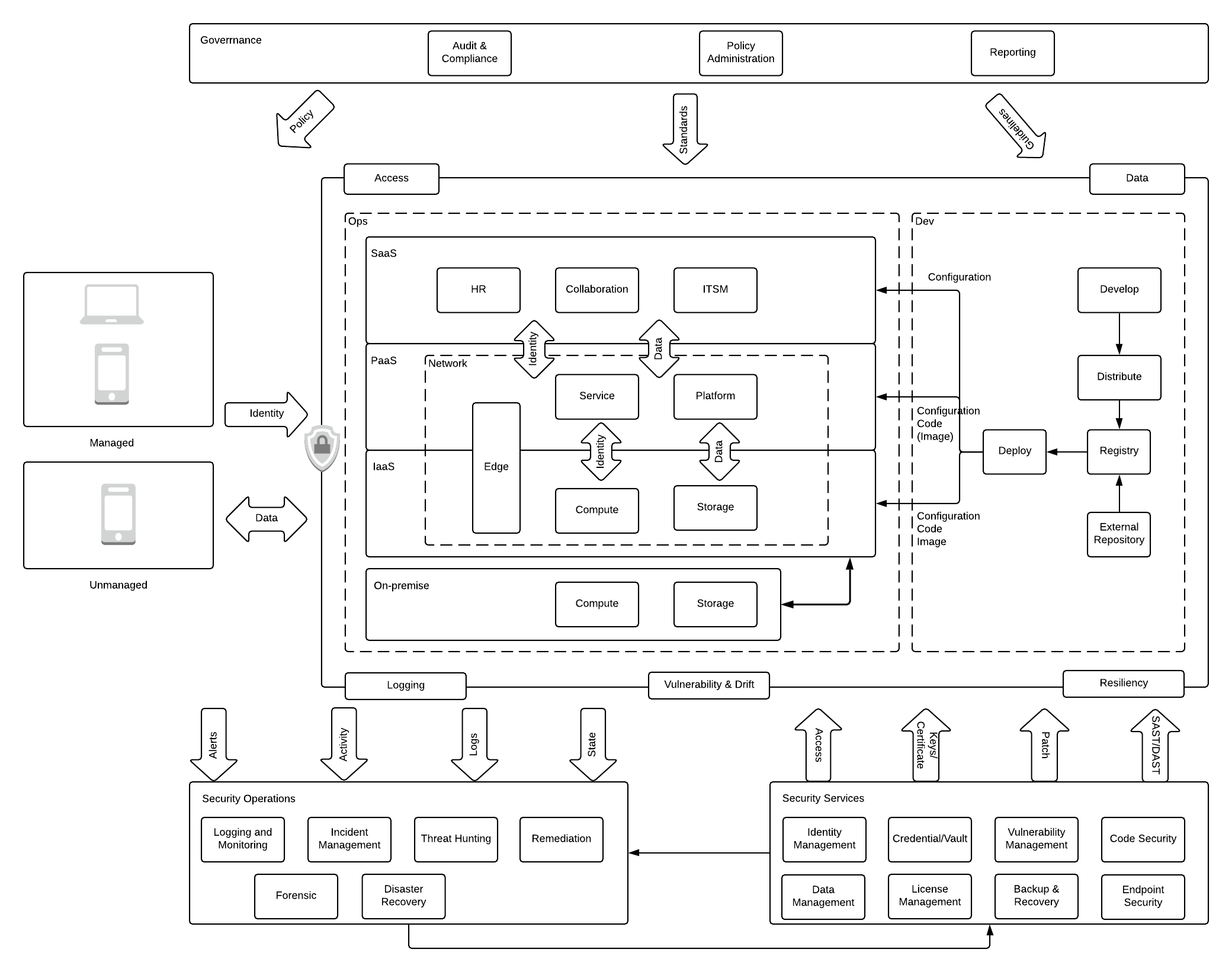
67. How We Built a Solution That Improves Google Cloud Security by Leveraging Managed Instance Groups
 Ckeckout some significant enhancements to CloudGuard’s integration with new and existing Google Cloud features to benefit from it.
Ckeckout some significant enhancements to CloudGuard’s integration with new and existing Google Cloud features to benefit from it.
68. Top 10 Cloud Security Trends of the Year
 While cloud security trends can come and go, there are some with great sticking power. The following top 10 cloud security trends need to be adopted in 2022.
While cloud security trends can come and go, there are some with great sticking power. The following top 10 cloud security trends need to be adopted in 2022.
69. Why You Should Adopt Cloud Computing in Healthcare
 Don’t rush into cloud migration without thorough preparation, assuming that cloud vendors will do you justice. Some of them might not even understand the specifics of your industry.This article will help you discover different cloud deployment models and recognize the risks associated with adopting cloud computing in healthcare. It will also give you some tips on how to get started.With this knowledge, you can turn to experts in technology solutions for healthcare to get more information on your preferred deployment model and to assist you with migration and custom software development, if needed.
Don’t rush into cloud migration without thorough preparation, assuming that cloud vendors will do you justice. Some of them might not even understand the specifics of your industry.This article will help you discover different cloud deployment models and recognize the risks associated with adopting cloud computing in healthcare. It will also give you some tips on how to get started.With this knowledge, you can turn to experts in technology solutions for healthcare to get more information on your preferred deployment model and to assist you with migration and custom software development, if needed.
Thank you for checking out the 69 most read stories about Cloud Security on HackerNoon.
Visit the /Learn Repo to find the most read stories about any technology.

