Let's learn about Network Security via these 59 free stories. They are ordered by most time reading created on HackerNoon. Visit the /Learn Repo to find the most read stories about any technology.
1. Top Open Source Vulnerabilities to Watch Out
 Open Source packages are a mainstay for most software engineering projects. We are so accustomed as developers to run our
Open Source packages are a mainstay for most software engineering projects. We are so accustomed as developers to run our npm install (for Node developers) or
2. Network Security: Things Most People Don’t Think About
 There are a lot of things most people do not think about that can dramatically increase the level of security on a network
There are a lot of things most people do not think about that can dramatically increase the level of security on a network
3. 3 Key Takeaways from Biden’s Cybersecurity Executive Order
 Learn more about the consequences of Biden's Executive Order on Improving the Nation’s Cybersecurity on software vendors and government contractors.
Learn more about the consequences of Biden's Executive Order on Improving the Nation’s Cybersecurity on software vendors and government contractors.
4. Replicate PostgreSQL Databases Using async Python and RabbitMQ for High Availability
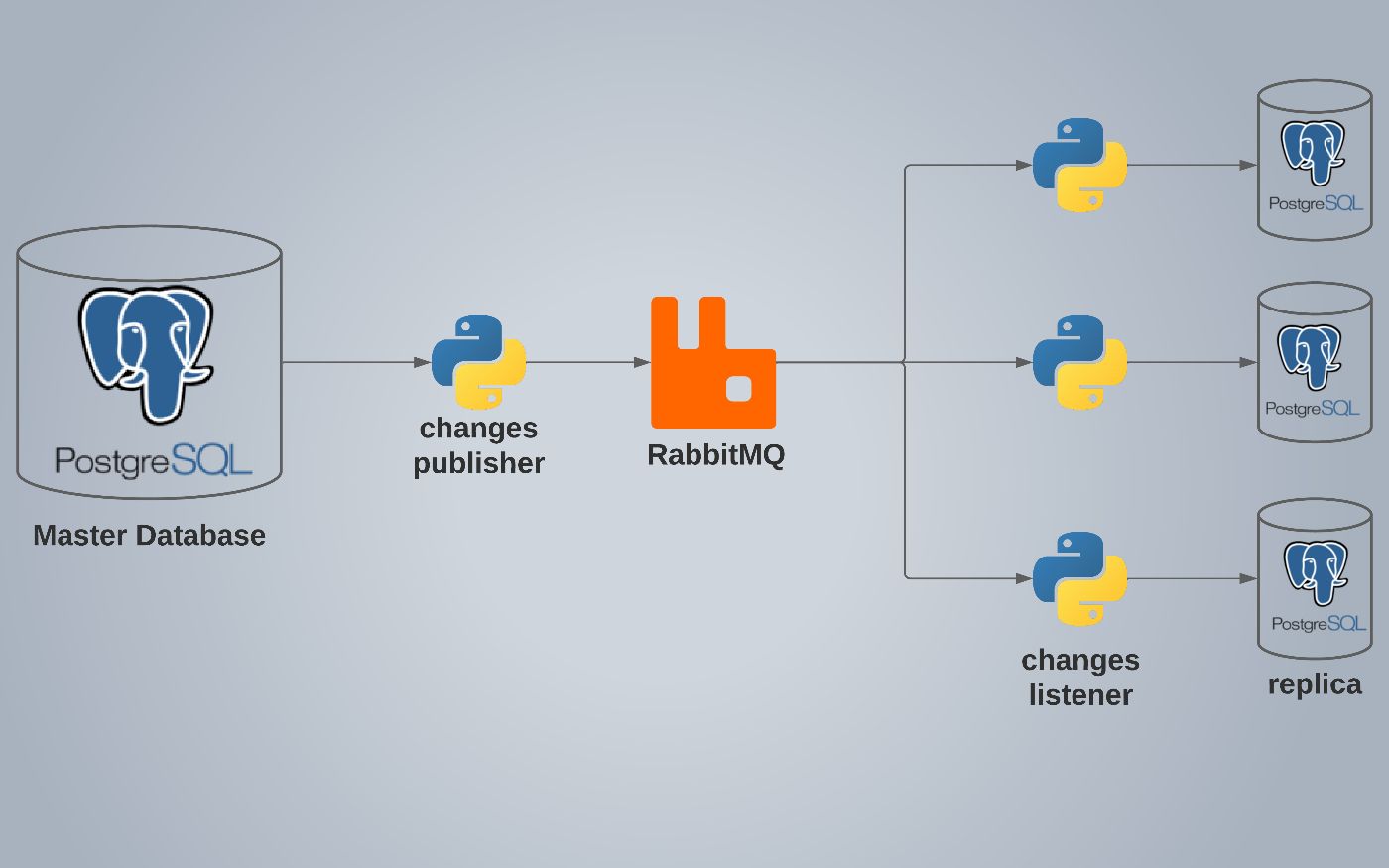 PostgreSQL replication using python and RabbitMQ for providing your database server with High Availability by easily making replicas of your master server.
PostgreSQL replication using python and RabbitMQ for providing your database server with High Availability by easily making replicas of your master server.
5. 8 Cybersecurity Tips Small Businesses Should Know
 Cyberattacks do not discriminate between industries, and no matter how big or tiny your organization is, it is vulnerable to them.
Cyberattacks do not discriminate between industries, and no matter how big or tiny your organization is, it is vulnerable to them.
6. Your Wi-Fi Cameras may be getting Attacked
 Your Wi-Fi security cameras are probably not secure. See how we disable our camera network with a simple DoS attack.
Your Wi-Fi security cameras are probably not secure. See how we disable our camera network with a simple DoS attack.
7. How DevOps Killed WAF
 Web Application Firewalls have been a key part of cybersecurity that are facing obsolencence thanks to the significant labour costs associated with WAFs.
Web Application Firewalls have been a key part of cybersecurity that are facing obsolencence thanks to the significant labour costs associated with WAFs.
8. Cracking the SANS GSEC Certification
 The SANS GIAC Security Essentials (GSEC) certification is for anyone working in the field of Information Security.
The SANS GIAC Security Essentials (GSEC) certification is for anyone working in the field of Information Security.
9. Top Signs that Indicate You Are About To Suffer a Cyber Breach
 There are few things worse than being told that your business’s security has been compromised. Organizations might not know that a security breach is taking place, or has been for some time. Yet, risk mitigation and technical safeguards are always getting better.
There are few things worse than being told that your business’s security has been compromised. Organizations might not know that a security breach is taking place, or has been for some time. Yet, risk mitigation and technical safeguards are always getting better.
10. Why Network Security is an Integral Part of Any Internet-Connected Business
 Network security is vital for any internet-connected company. Without it, hackers can steal all the data the business has. Bad network security causes problems
Network security is vital for any internet-connected company. Without it, hackers can steal all the data the business has. Bad network security causes problems
11. Man In The Middle Attack Using Bettercap Framework
 Man-in-the-middle attack (MITM) is an attack where the attacker secretly relays and possibly alters the communications between two devices who believe that they are directly communicating with each other. In order to perform man in the middle attack, we need to be in the same network as our victim because we have to fool these two devices. Now lets initiate the attack by running our tools which is bettercap. To run bettercap we can simply open up terminal and type bettercap -iface [your network interface which connected to the network]. To know which network interface is used we can simply type ifconfig and here is what it shows us.
Man-in-the-middle attack (MITM) is an attack where the attacker secretly relays and possibly alters the communications between two devices who believe that they are directly communicating with each other. In order to perform man in the middle attack, we need to be in the same network as our victim because we have to fool these two devices. Now lets initiate the attack by running our tools which is bettercap. To run bettercap we can simply open up terminal and type bettercap -iface [your network interface which connected to the network]. To know which network interface is used we can simply type ifconfig and here is what it shows us.
12. 4 Reasons To Learn Ethical Hacking
 In the digital world, cybersecurity and ethical hacking are arising as promising career options for IT professionals.
In the digital world, cybersecurity and ethical hacking are arising as promising career options for IT professionals.
13. 5 Types of Cyber Security and Why It’s Important to be Aware of Them
 Cybersecurity is the process of protecting systems, networks, and programs from malicious attacks. But why is it important? Let’s find out.
Cybersecurity is the process of protecting systems, networks, and programs from malicious attacks. But why is it important? Let’s find out.
14. An Introduction to Malware Analysis
 Malicious software (Malware) are either programs or files that are intended to cause harm to a system and thereby its user.
Malicious software (Malware) are either programs or files that are intended to cause harm to a system and thereby its user.
15. How I Created a Zero Trust Overlay Network in my Home
 Enabling a secure home automation experience, by creating a zero trust overlay network to access #HomeAssistant.
Enabling a secure home automation experience, by creating a zero trust overlay network to access #HomeAssistant.
16. Fighting the Hydra of DDoS Attacks (Spoiler: They Got Worse)
 Interview with Link11 regarding their new DDoS report -- the state of DDoS attacks.
Interview with Link11 regarding their new DDoS report -- the state of DDoS attacks.
17. Do I Need A Degree To Become A Cybersecurity Professional?
 Do you need a degree to get started in cybersecurity? And do you need a degree to progress in cybersecurity? The answer is both yes and no.
Do you need a degree to get started in cybersecurity? And do you need a degree to progress in cybersecurity? The answer is both yes and no.
18. DNS Queries Explained
 DNS is a topic often considered difficult to understand, but the basic workings are actually not hard to grasp. The first fundamental point to grasp is that every domain in existence is linked to an Internet Protocol (IP) address.
DNS is a topic often considered difficult to understand, but the basic workings are actually not hard to grasp. The first fundamental point to grasp is that every domain in existence is linked to an Internet Protocol (IP) address.
19. Why 5G Security Will Suffer From 4G Vulnerabilities
 The fifth generation of mobile communication networks isn’t on its way; it's already here. You’ve probably heard plenty about 5G in the past few years, as this promising new generation of wireless technology is what’s enabling the continued spread of the internet of things and a host of other digital innovations. Virtually all tech experts agree that 5G technology is a good thing, given that it will lead to faster connectivity and more secure networks. However, there are good reasons to believe that the staggered deployment of 5G technology will mean that it remains vulnerable to a number of security woes currently plaguing 4G technology.
The fifth generation of mobile communication networks isn’t on its way; it's already here. You’ve probably heard plenty about 5G in the past few years, as this promising new generation of wireless technology is what’s enabling the continued spread of the internet of things and a host of other digital innovations. Virtually all tech experts agree that 5G technology is a good thing, given that it will lead to faster connectivity and more secure networks. However, there are good reasons to believe that the staggered deployment of 5G technology will mean that it remains vulnerable to a number of security woes currently plaguing 4G technology.
20. How to Make a Malicious USB Device and Have Some Harmless Fun
 Make an inexpensive BadUSB from an old USB drive and learn about Windows shortcut files and how malicious actors are using .lnk files to spread malware.
Make an inexpensive BadUSB from an old USB drive and learn about Windows shortcut files and how malicious actors are using .lnk files to spread malware.
21. Getting started with NMAP (Network Mapper)
 “The quieter you become the more you are able to hear”
“The quieter you become the more you are able to hear”
22. RBAC and PSPs Can Only Bring Your Kubernetes Security So Far
 Admins need to defend their organizations against a Kubernetes security incident. RBAC and PSPs will only get them so far; more security measures are needed.
Admins need to defend their organizations against a Kubernetes security incident. RBAC and PSPs will only get them so far; more security measures are needed.
23. Your Ultimate Guide To The 4 Types of IT Security
 IT Security protects your business against cyber threats. There are four types of IT Security: network security, end-point security, internet & cloud security.
IT Security protects your business against cyber threats. There are four types of IT Security: network security, end-point security, internet & cloud security.
24. Reference Architecture for Network Secured Azure Web App
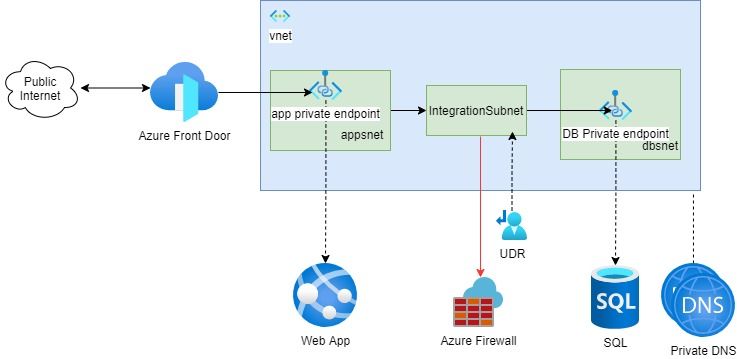 Cloud solution architecture of Azure hosted web application from Network Security perspective using Azure App Service, Azure SQL using Private Endpoints
Cloud solution architecture of Azure hosted web application from Network Security perspective using Azure App Service, Azure SQL using Private Endpoints
25. Network Security vs. Cybersecurity: What's the Difference?
 While network security is a separate and important subset, cybersecurity covers a broader whole in terms of security.
While network security is a separate and important subset, cybersecurity covers a broader whole in terms of security.
26. Meet the Writer: HackerNoon Contributor Jessica Truong Talks Cybersecurity
 Meet Jessica! She is a Cybersecurity enthusiast whose goal is to educate readers of the different topics within Cybersecurity. Check out her HN page for more!
Meet Jessica! She is a Cybersecurity enthusiast whose goal is to educate readers of the different topics within Cybersecurity. Check out her HN page for more!
27. What is Subdomain Hijacking and How to Prevent it?
 Subdomain takeover or subdomain hijacking refers to a technique by which "unused" subdomains can be made to point to a location of the attacker's choice.
Subdomain takeover or subdomain hijacking refers to a technique by which "unused" subdomains can be made to point to a location of the attacker's choice.
28. How to Protect Your Company's VPN When You Have a Remote Team
 Prevent malicious agents from exploiting their VPN connections! However, it's still critical for each employee to exercise cyber hygiene to ensure cybersecurity
Prevent malicious agents from exploiting their VPN connections! However, it's still critical for each employee to exercise cyber hygiene to ensure cybersecurity
29. Firewall Configuration: 6 Best Practices to Secure a Business Network
 Business success relies on network security. Here are six best practices to secure a business network.
Business success relies on network security. Here are six best practices to secure a business network.
30. IT Security: How to Deal With The Insider Threat
 A study by the Wall Street Journal found that almost 70% of companies admitted concern about violent employees! While workers continue to be a major security ri
A study by the Wall Street Journal found that almost 70% of companies admitted concern about violent employees! While workers continue to be a major security ri
31. Startup Interview with Tracie Thompson, HackHunter CEO
 HackHunter was nominated as one of the best startups in Docklands, Australia in in HackerNoon’s Startup of the Year. This is interview with their CEO.
HackHunter was nominated as one of the best startups in Docklands, Australia in in HackerNoon’s Startup of the Year. This is interview with their CEO.
32. Improve Kubernetes Network Security with Cilium
 This article will show how to, using Cilium, tackle the authorization concern and move to push it to the underlying platform from the application code.
This article will show how to, using Cilium, tackle the authorization concern and move to push it to the underlying platform from the application code.
33. Network Scanner Working and Implementation
 In this blog, we will see how a network mapper works and how we can implement these network security tools in Python for our cybersecurity related projects
In this blog, we will see how a network mapper works and how we can implement these network security tools in Python for our cybersecurity related projects
34. 5 Popular Types of Penetration Testing for SaaS Businesses
 If you are running a SaaS business, you know that security is everything. Nowadays, we can see many different cyberattacks and their variants targeting SaaS.
If you are running a SaaS business, you know that security is everything. Nowadays, we can see many different cyberattacks and their variants targeting SaaS.
35. Life-Changing Facts About Apple’s iOS Security Architecture
 Introduction to Apple platform security:
Introduction to Apple platform security:
36. Best Practices for API Security

Yet, its open doors and wide visibility makes it vulnerable to attacks. Also, attackers can easily find the way to the heart of applications and systems via APIs. Hence it is essential to fence APIs with all possible measures.
37. Cybersecurity Basics, Tech Education and Market Review

38. An Unboring Guide to Endpoint Detection and Response (EDR)
 EDR solutions detect, investigate & eliminate threats as quickly as possible. It generates alerts to notify security professionals so that they can investigate.
EDR solutions detect, investigate & eliminate threats as quickly as possible. It generates alerts to notify security professionals so that they can investigate.
39. IoT Matters in 2021: IoT-Enabled Smart Office Automation to Work and Collect Data Human-Free
 An engineering approach to building IoT software like smart office ecosystem and IoT security concerns for smart office applications.
An engineering approach to building IoT software like smart office ecosystem and IoT security concerns for smart office applications.
40. An Introduction to Layer 3 Switches
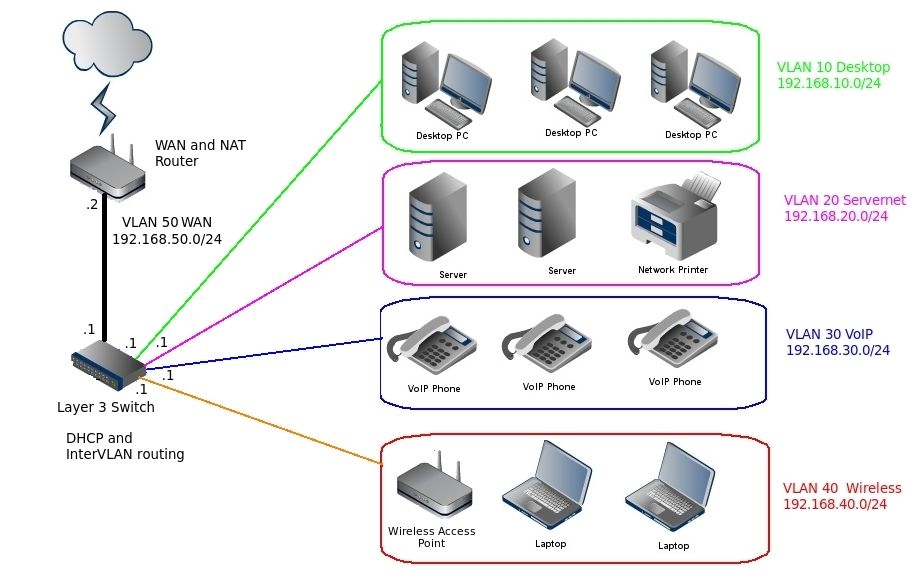 In today's complex business networks that comprise many virtual LAN's and subnets, a Layer 3 switch plays an important role in many systems. But do you need this on your network? Let's see.
In today's complex business networks that comprise many virtual LAN's and subnets, a Layer 3 switch plays an important role in many systems. But do you need this on your network? Let's see.
41. How to Improve Network Security and Visibility in 2020 and 2021
 With the number of products available, it can be an uphill task to try to ensure robust network security and visibility. This, however, is a task that must be accomplished if you want to be competitive.
With the number of products available, it can be an uphill task to try to ensure robust network security and visibility. This, however, is a task that must be accomplished if you want to be competitive.
42. An Introductory Guide to Hacking NETBIOS
 When a hacker spots a system with open ports supporting NetBios, the hopes go high! Let's start by understanding the the nitty-gritty of NETBIOS.
When a hacker spots a system with open ports supporting NetBios, the hopes go high! Let's start by understanding the the nitty-gritty of NETBIOS.
43. Why OpenTelemetry Should Matter to Network and Systems Admins
 OpenTelemetry is young, even by internet standards. Born out of the merger of OpenTracing and OpenCensus projects at the Cloud Native Computing Foundation CNCF
OpenTelemetry is young, even by internet standards. Born out of the merger of OpenTracing and OpenCensus projects at the Cloud Native Computing Foundation CNCF
44. Network Security 101: Everything You Need to Know
 Network Security is Vital. Its purpose is to prevent unauthorized users from accessing an organization's network and devices. It is intended to keep data safe.
Network Security is Vital. Its purpose is to prevent unauthorized users from accessing an organization's network and devices. It is intended to keep data safe.
45. Are VPNs Really Safe?
 Virtual Private Network (VPN) cloaks your online identity, and shielding your data from prying eyes.
Virtual Private Network (VPN) cloaks your online identity, and shielding your data from prying eyes.
46. Identify Wechat's TxBugReport File on your PC Through These Simple Steps
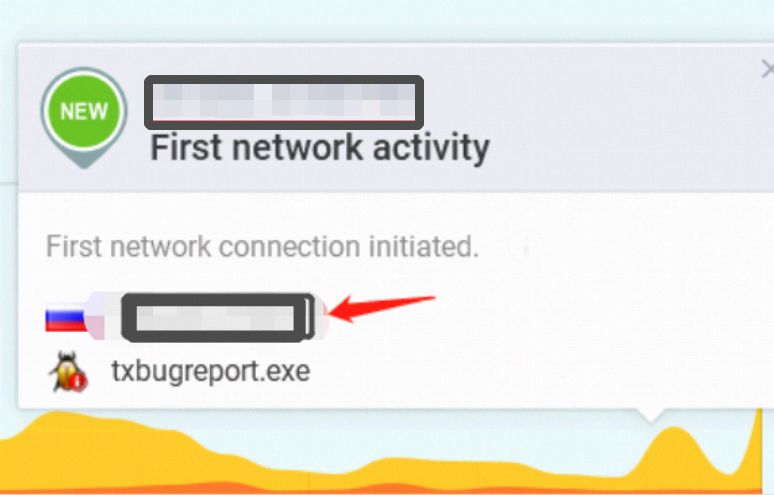 In this post, we will learn easy steps to turn off the txbugreport.exe process running in your Computer and occupying more memory and prevent this .exe file from sending automated bug reports to Tencent Computer Systems.
In this post, we will learn easy steps to turn off the txbugreport.exe process running in your Computer and occupying more memory and prevent this .exe file from sending automated bug reports to Tencent Computer Systems.
47. How to Be Careful When Sharing WiFi Password With QR Code
 Share your QR code of your network carefully, mistakes can lead to disaster
Share your QR code of your network carefully, mistakes can lead to disaster
48. Understanding What Security Testing Is & Its Importance with The Top Tools and Key Principles
 In this article, we will explore what security testing is, the top tools for security testing, and the key principles of security testing.
In this article, we will explore what security testing is, the top tools for security testing, and the key principles of security testing.
49. PoW Shield: An Application Layer Proof of Work DDoS Filter
 PoW Shield provides DDoS protection on the OSI application layer by authenticating traffic using a simple proof-of-work validation process.
PoW Shield provides DDoS protection on the OSI application layer by authenticating traffic using a simple proof-of-work validation process.
50. Discovering 10 Cybersecurity Practices for Enhanced IT Infrastructure Protection
 The need to have secure IT Infrastructure is common for all companies worldwide. Learn the best cybersecurity practices to get yourself protected from hacking.
The need to have secure IT Infrastructure is common for all companies worldwide. Learn the best cybersecurity practices to get yourself protected from hacking.
51. Understanding & Recognizing Different Cyber Threats: What to Look Out For
 This article will dive into understanding & recognizing some cyber threats. It will not cover every example for each attack or every attack.
This article will dive into understanding & recognizing some cyber threats. It will not cover every example for each attack or every attack.
52. Network Security Basics
 Ever since the creation of the internet with all of the good that it has brought to the table came the bad as well. In the age of information technology, an unsecured product is a surefire way to numerous issues. A company, which creates a product has to make sure both the software and the network security features of it are as robust as possible. In the previous article we discussed application security, however, it is never complete without a clear network safeguards to serve as a frontline against malicious users trying to exploit the system. But what is network security and what are some of the methods used to protect systems?
Ever since the creation of the internet with all of the good that it has brought to the table came the bad as well. In the age of information technology, an unsecured product is a surefire way to numerous issues. A company, which creates a product has to make sure both the software and the network security features of it are as robust as possible. In the previous article we discussed application security, however, it is never complete without a clear network safeguards to serve as a frontline against malicious users trying to exploit the system. But what is network security and what are some of the methods used to protect systems?
53. What is BGP Hijacking and How Do You Prevent It?
 BGP, which stands for Border Gateway Protocol, is a path vector routing protocol that is used to connect external organizations to each other.
BGP, which stands for Border Gateway Protocol, is a path vector routing protocol that is used to connect external organizations to each other.
54. What Are The Cybersecurity Risks Associated With Personal Devices?
 Let's look at some of the most significant risks posed by your personal digital devices, and what we can do to boost your security.
Let's look at some of the most significant risks posed by your personal digital devices, and what we can do to boost your security.
55. 5 Best Free Proxy Servers To Visit Sites Anonymously In 2020
 A proxy server will assist you to mask your identity on the web. Perhaps you wish to access suspicious websites, bypass net censorship in your country or on your office/school network having a proxy website among your reach is very important.
A proxy server will assist you to mask your identity on the web. Perhaps you wish to access suspicious websites, bypass net censorship in your country or on your office/school network having a proxy website among your reach is very important.
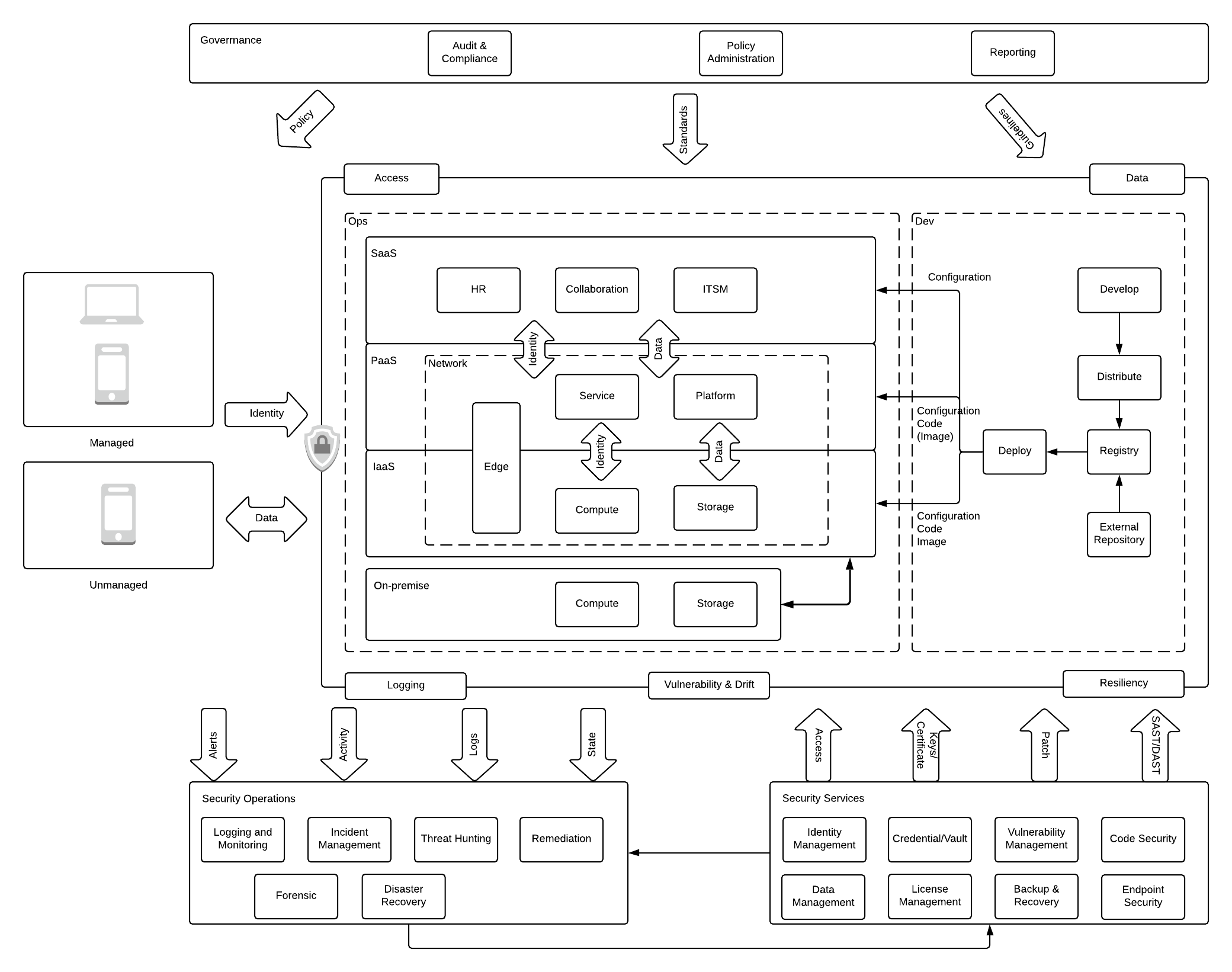
56. Enterprise Cloud Security: Setting Up Structure, Identity-Based Access, and Network Control
57. Top Penetration Testing Tools for Professionals
 Looking for penetration testing tools, which is good. Here is the list of some best tools with comparison. Check out this post.
Looking for penetration testing tools, which is good. Here is the list of some best tools with comparison. Check out this post.
58. WTF is Internet Of Bio Nano Things (IoBNT) and How Secure Is It?

59. 7 Ways to Protect Your Router From Hackers
 Since we are in the modern technological era, the internet has become an indispensable tool in our modern-day life. As we speak, we need it to communicate, work online, learn online and even do business online. When it comes to internet connectivity, there are many ways to get internet in your home. One of the best ways to access the internet at home or workplace is by investing in a router. With this device in place, you will be able to create a home network that can be used by wireless devices such as smart TVs, home appliances, IP cameras, and so much more.
Since we are in the modern technological era, the internet has become an indispensable tool in our modern-day life. As we speak, we need it to communicate, work online, learn online and even do business online. When it comes to internet connectivity, there are many ways to get internet in your home. One of the best ways to access the internet at home or workplace is by investing in a router. With this device in place, you will be able to create a home network that can be used by wireless devices such as smart TVs, home appliances, IP cameras, and so much more.
Thank you for checking out the 59 most read stories about Network Security on HackerNoon.
Visit the /Learn Repo to find the most read stories about any technology.

