Let's learn about Authentication via these 161 free stories. They are ordered by most time reading created on HackerNoon. Visit the /Learn Repo to find the most read stories about any technology.
1. Set up a Flutter app and Implement Google Sign-In Using Firebase
 How to set up a Flutter app and implement Google sign-in using Firebase.
How to set up a Flutter app and implement Google sign-in using Firebase.
2. The Good Things, and the Not So Good Things, About Working With Firebase
 Most of the developers have heard for Google’s product called Firebase. It’s, how Google says “mobile platform that helps you quickly develop high-quality apps and grow your business.“. It’s basically a set of tools that most developers will need when building an app. In this article I’ll go over these tools, and point all the things you need to know if you choose to use Firebase.
Most of the developers have heard for Google’s product called Firebase. It’s, how Google says “mobile platform that helps you quickly develop high-quality apps and grow your business.“. It’s basically a set of tools that most developers will need when building an app. In this article I’ll go over these tools, and point all the things you need to know if you choose to use Firebase.
3. About History and Irony of Logging (in)
 The story of event logging begins at sea and is related to navigation. One of the important aspects of navigation is <a href="https://en.wikipedia.org/wiki/Dead_reckoning" target="_blank">dead reckoning</a>: estimating your current position based on course, speed and time from a known, observed point. In the end of 15th century, speed at sea was measured with a small wooden log. A so-called ‘Dutchman’s Log’ was dropped overboard from the bow of the ship and the navigator measured the time elapsing before it passed the stern.
The story of event logging begins at sea and is related to navigation. One of the important aspects of navigation is <a href="https://en.wikipedia.org/wiki/Dead_reckoning" target="_blank">dead reckoning</a>: estimating your current position based on course, speed and time from a known, observed point. In the end of 15th century, speed at sea was measured with a small wooden log. A so-called ‘Dutchman’s Log’ was dropped overboard from the bow of the ship and the navigator measured the time elapsing before it passed the stern.
4. The Simple & Efficient Way to Enable JWT auth in Laravel By Using PHP-JWT Module
 I encounter this issue while working on an application for a client recently. Instead of using a JWT library build for Laravel, I used firebase/php-jwt to generate and authenticate users. Don’t ask why as there were many reasons behind this decision. If you are using any Laravel library for JWT like tymondesigns/jwt-auth then you don’t need this anyway, use the library if you want.
I encounter this issue while working on an application for a client recently. Instead of using a JWT library build for Laravel, I used firebase/php-jwt to generate and authenticate users. Don’t ask why as there were many reasons behind this decision. If you are using any Laravel library for JWT like tymondesigns/jwt-auth then you don’t need this anyway, use the library if you want.
5. How to Integrate ‘devise’ and ‘omniauth-facebook’ Authentication To Your Rails App

6. How to Build a Smooth Authentication Flow System with Firebase
 This tutorial involves going through a step-by-step guide on how to set up the Firebase authentication service, and then a walk-through of how to implement it.
This tutorial involves going through a step-by-step guide on how to set up the Firebase authentication service, and then a walk-through of how to implement it.
7. An Essential Guide to IAM (Identity Access Management) in 2022
 The term IAM is one of the common you hear in cloud-native environments. What does such a system do? A fast and pragmatic introduction to IAM
The term IAM is one of the common you hear in cloud-native environments. What does such a system do? A fast and pragmatic introduction to IAM
8. JSON Web Token: How To Secure Your Data With JWT

9. Auth0 vs Okta vs Cognito vs SuperTokens Compared (2022)
 An in depth review of Auth0 alternatives for 2022: Auth0 vs Okta vs Cognito vs SuperTokens
An in depth review of Auth0 alternatives for 2022: Auth0 vs Okta vs Cognito vs SuperTokens
10. How SuperTokens' Pre Built UI Can Be Used With VueJS
 Protect your VueJs app with SuperTokens by easily adding authentication with pre-built and session management to your project right out of the box easily.
Protect your VueJs app with SuperTokens by easily adding authentication with pre-built and session management to your project right out of the box easily.
11. From A to Z: The ABCs of Secure Authentication for Enterprises
 Having secure authentication measures in place isn't optional. We cover everything your organization needs to know about secure authentication from A to Z.
Having secure authentication measures in place isn't optional. We cover everything your organization needs to know about secure authentication from A to Z.
12. Why You Should Use IAM Policies to Enforce MFA on AWS
 In my past life, I was an auditor and performed hundreds of cybersecurity
readiness assessments. These were sometimes called “gap analysis” and
the essential purpose of these assessments were to provide organizations with the answers to the test for their upcoming official assessment.
In my past life, I was an auditor and performed hundreds of cybersecurity
readiness assessments. These were sometimes called “gap analysis” and
the essential purpose of these assessments were to provide organizations with the answers to the test for their upcoming official assessment.
13. How to Authenticate Your Git to GitHub with SSH Keys
 Authenticate your local machine git's to GitHub using SSH authentication. You do not need to type username and password anymore with this easy addition.
Authenticate your local machine git's to GitHub using SSH authentication. You do not need to type username and password anymore with this easy addition.
14. What Developers Mean When They Talk About API
 API has become one of those catch-all terms that developers throw around without really considering the context. On any given week, you will come across discussions like "How to use the Twitter API", "New framework X is great because it has a low API surface", and "Best practices for building an API."
API has become one of those catch-all terms that developers throw around without really considering the context. On any given week, you will come across discussions like "How to use the Twitter API", "New framework X is great because it has a low API surface", and "Best practices for building an API."
15. The Future of Authentication

16. Google's Authenticator App Explained and Reviewed
17. Secure Sessions in JavaScript: Forking Express-Session to Improve Security
 If you ever made a webapp in JS, chances are you used Express as a web framework, Passport for user authentication and express-session to maintain users logged in. This article focuses on sessions and how we forked express-session to make it more secure.
If you ever made a webapp in JS, chances are you used Express as a web framework, Passport for user authentication and express-session to maintain users logged in. This article focuses on sessions and how we forked express-session to make it more secure.
18. Authentication Using the Auth0 to a React Application
 Application example built with React with authentication using the Auth0 service.
Application example built with React with authentication using the Auth0 service.
19. How to Implement One Tap Google Sign-In With Ruby on Rails
 In this blog post, we will discuss how to integrate Google Identity Services into any of your front-end applications.
In this blog post, we will discuss how to integrate Google Identity Services into any of your front-end applications.
20. How Can You Improve Your Cybersecurity With Continuous Authentication
 Standard authentication methods such as multi-factor authentication (MFA) and one-time passwords work as filters at the entrance of the protected perimeter. But what if someone managed to trick these filters or changed the user after their successful login? Cyber attackers may steal credentials of legitimate users and even one-time passcodes using malware and different phishing techniques. In the companies without special employee monitoring software, employees often nonchalantly share their logins and passwords with colleagues. Finally, there’s always a risk of someone getting a hold of a corporate device such as a laptop or smartphone with full access to the corporate network, critical resources, and applications.
Standard authentication methods such as multi-factor authentication (MFA) and one-time passwords work as filters at the entrance of the protected perimeter. But what if someone managed to trick these filters or changed the user after their successful login? Cyber attackers may steal credentials of legitimate users and even one-time passcodes using malware and different phishing techniques. In the companies without special employee monitoring software, employees often nonchalantly share their logins and passwords with colleagues. Finally, there’s always a risk of someone getting a hold of a corporate device such as a laptop or smartphone with full access to the corporate network, critical resources, and applications.
21. How to Secure Your Flask Application with Ory Kratos and Ory Keto
 How to secure a flask application using Ory Kratos and Keto to easily add authentication features into your program without needing lines and lines of code.
How to secure a flask application using Ory Kratos and Keto to easily add authentication features into your program without needing lines and lines of code.
22. Nextjs User Login Authentication in 5 Simple Steps Using Auth0
 In this post we are going to discuss, how you can set up a user Login authentication using Auth0 in Next.js projects.
In this post we are going to discuss, how you can set up a user Login authentication using Auth0 in Next.js projects.
23. Application Authentication: AWS Cognito vs JSON Web Token
 Explore the difference between two well-known Auth building methods: AWS Cognito and JSON Web Token. Plus, take a look at the AWS Cognito application process.
Explore the difference between two well-known Auth building methods: AWS Cognito and JSON Web Token. Plus, take a look at the AWS Cognito application process.
24. An Overview of OAuth Fundamentals and Flows
 OAuth flows are essentially OAuth-supported methods for verifying permissions and resource owner information.
OAuth flows are essentially OAuth-supported methods for verifying permissions and resource owner information.
25. Using $auth Module’s Redirect in Tandem With $router.push in Nuxt.js
 Recently I came across the issue of using the auth module in Nuxt.js and invoking a $router.push in subsequent line of code in the same method. The conundrum began when the lines after the auth.loginWith method did not execute as intended since the page was redirected to the redirect URI.
Recently I came across the issue of using the auth module in Nuxt.js and invoking a $router.push in subsequent line of code in the same method. The conundrum began when the lines after the auth.loginWith method did not execute as intended since the page was redirected to the redirect URI.
26. Using SuperTokens in a VueJS App With Your Own UI
 Learn how to build your own login UI with SuperTokens in your VueJS application.
Learn how to build your own login UI with SuperTokens in your VueJS application.
27. Extending Your Login Flow With Auth0 Actions
 In this article, I am going to explain what is Auth0 Actions, why to use them, and how to set one up.
In this article, I am going to explain what is Auth0 Actions, why to use them, and how to set one up.
28. Random Password Generator Command in Linux we Rarely Use
 Password generators are now in abundance. Particularly surprising are the many web applications for this purpose.
Password generators are now in abundance. Particularly surprising are the many web applications for this purpose.
29. Express-js Boilerplate with User Authentication
30. A Quick Guide to JSON Web Token [JWT]
 JSON Web Token (JWT) is an open standard (RFC 7519) for securely transmitting information between parties as JSON objects.
JSON Web Token (JWT) is an open standard (RFC 7519) for securely transmitting information between parties as JSON objects.
31. HELP! There’s a JWT in my Metaverse!
 Are JWTs really dead, or are they just misunderstood? In this article, Patrick Lee Scott explores the usage of JWTs in a web3 world.
Are JWTs really dead, or are they just misunderstood? In this article, Patrick Lee Scott explores the usage of JWTs in a web3 world.
32. Passwordless vs MFA: The Future of Authentication
 A passwordless approach is not the end-all-be-all for data security, but it is the start of establishing a single, strong user identity and trust.
A passwordless approach is not the end-all-be-all for data security, but it is the start of establishing a single, strong user identity and trust.
33. SSO Infrastructure Cyber Attacks - Learn How to Detect Early and Mitigate the Risk
 With the increasing cybersecurity threats, businesses are now more concerned about cybersecurity hygiene and are swiftly adopting security mechanisms, like single sign-on (SSO).
With the increasing cybersecurity threats, businesses are now more concerned about cybersecurity hygiene and are swiftly adopting security mechanisms, like single sign-on (SSO).
34. Protecting Your Supabase App With SuperTokens Authentication
 Learn reasons why you should choose SuperTokens as your auth provider and why it pairs so well with Supabase in protecting you and your online infrastructure
Learn reasons why you should choose SuperTokens as your auth provider and why it pairs so well with Supabase in protecting you and your online infrastructure
35. What Makes Zero Trust Better And Different From Traditional Security
 Traditional vs zero trust? Learn how zero trust outperforms the traditional model by delivering improved security, flexibility and reduced complexity.
Traditional vs zero trust? Learn how zero trust outperforms the traditional model by delivering improved security, flexibility and reduced complexity.
36. An Introduction to Code Signing Architectures and Techniques

37. Digital Identity Around the World: Why Some Countries are Embracing Self Sovereign Identity Quicker
 This article outlines the questions and logistics to consider when countries adopt or adapt new privacy laws and self-sovereign identity.
This article outlines the questions and logistics to consider when countries adopt or adapt new privacy laws and self-sovereign identity.
38. Are Social Logins More Secure?
 Social logins are more secure than the traditional username/password.
Social logins are more secure than the traditional username/password.
39. What Is a JSON Web Token (JWT)?
 JWTs or JSON Web Tokens are most commonly used to identify an authenticated user. They are issued by an authentication server and are consumed by the client-ser
JWTs or JSON Web Tokens are most commonly used to identify an authenticated user. They are issued by an authentication server and are consumed by the client-ser
40. Building a Simple Session Based Authentication using Ruby on Rails
 Building your first authentication system may look intimidating at first. But to be honest, it's really easy. After reading this article, you will know how easy it is to create a session based authentication in rails.
Building your first authentication system may look intimidating at first. But to be honest, it's really easy. After reading this article, you will know how easy it is to create a session based authentication in rails.
41. What is OAuth (Open Authorization) and Why is it Important?
 First of all, we want the users to be authenticated - confirming that the users are who they say they are. Then, authorize them - to enable selective access.
First of all, we want the users to be authenticated - confirming that the users are who they say they are. Then, authorize them - to enable selective access.
42. Jwenky: An Express API Server with User Authentication
43. Authentication using the Auth0 to an Angular application
 Application example built with Angular 14 with authentication using the Auth0 service.
Application example built with Angular 14 with authentication using the Auth0 service.
44. My Journey Integrating Google Calendar (G-suite) in Node
 In this article, I’ll walk you through the agony of consuming Google Calendar API in Node with non-existent documentation. Particularly, accessing data using service account with domain-wide authority.
In this article, I’ll walk you through the agony of consuming Google Calendar API in Node with non-existent documentation. Particularly, accessing data using service account with domain-wide authority.
45. Mutual Human Authorization: A New Standard in Data Privacy
 Mutual Human Authorization is a digital communication protocol that SharePass is pioneering to help address persistent data privacy and security gaps.
Mutual Human Authorization is a digital communication protocol that SharePass is pioneering to help address persistent data privacy and security gaps.
46. YubiKey Introduction: GCP Service Account Key Generator

47. Using Devise In Your Ruby on Rails Application [A Step-by-Step Guide]
48. How to Hide Credentials in Spring Boot
 Use env properties in spring boot to add the environment variables.
Use env properties in spring boot to add the environment variables.
49. How to connect SuperTokens to a MySQL or to a PostgreSQL database
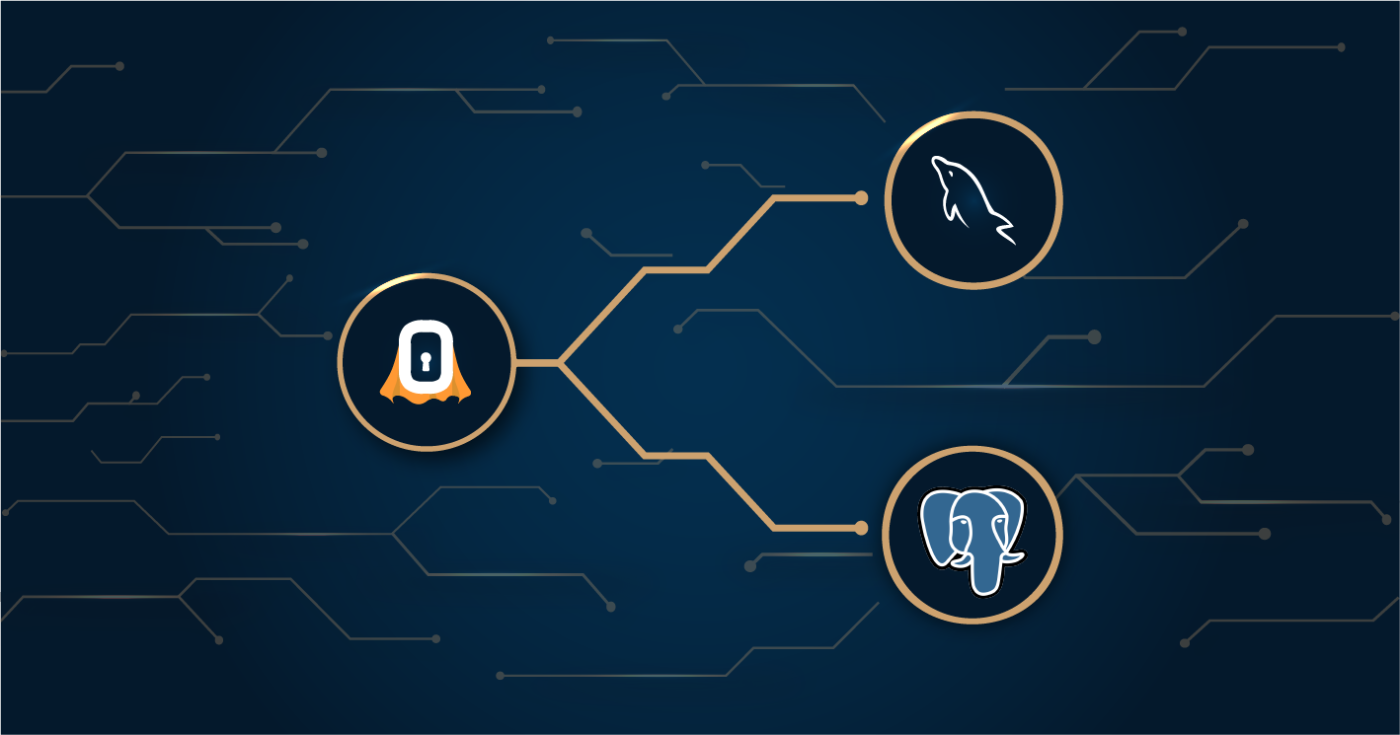 Learn how to connect a self-hosted SuperTokens core to a database with or without Docker
Learn how to connect a self-hosted SuperTokens core to a database with or without Docker
50. How to Add Authentication to a Full Stack MERN Web Application
 This article is part 2 of "Let's build and deploy a full stack MERN web application".
This article is part 2 of "Let's build and deploy a full stack MERN web application".
51. Authentication: Create a Simple Rick and Morty Wiki Page
 Authentication is the most important part of any application. Learn more about it!
Authentication is the most important part of any application. Learn more about it!
52. From Passwords to Passwordless Authentication
 Passwordless authentication is gradually replacing the password-based authentication practice. The CIA triad of Cybersecurity is changing rapidly. Learn how.
Passwordless authentication is gradually replacing the password-based authentication practice. The CIA triad of Cybersecurity is changing rapidly. Learn how.
53. How to Build A Passwordless Authentication with Email and JWT
 In this quick article, you'll see how to prevent one of the OWASP Top 10 security issues for websites: authentication that hasn't been implemented correctly.
In this quick article, you'll see how to prevent one of the OWASP Top 10 security issues for websites: authentication that hasn't been implemented correctly.
54. Understanding Roles-Based Access Control (RBAC)
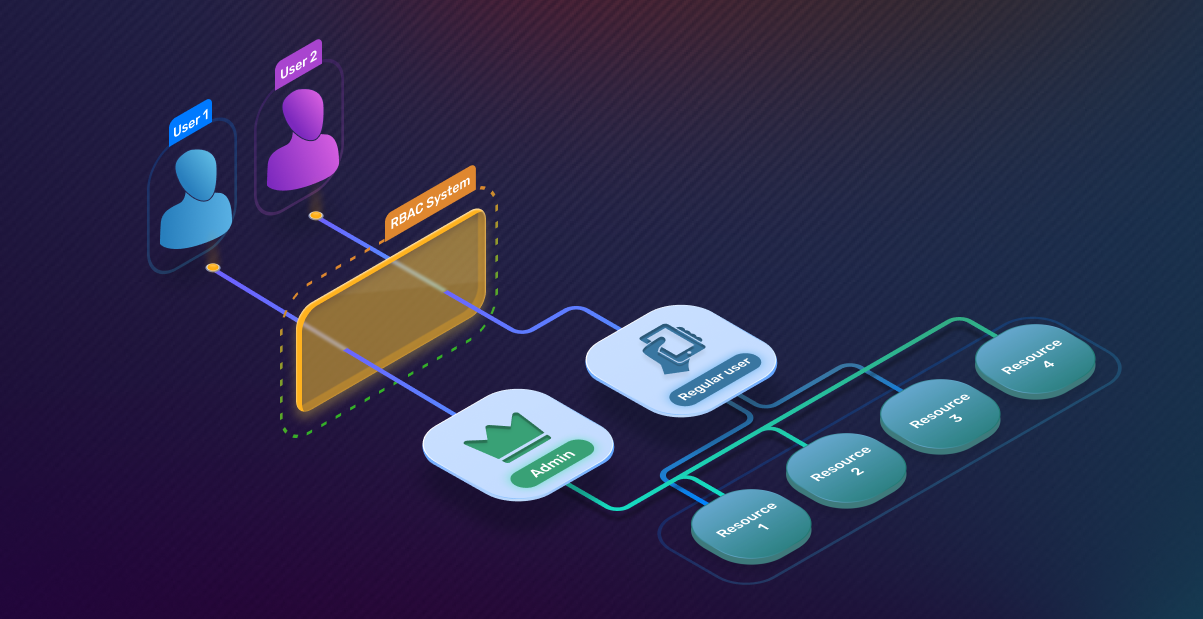 Learn about RBAC and advantages + disadvantages compared to ABAC.
Learn about RBAC and advantages + disadvantages compared to ABAC.
55. How I Built a Static Website with User Authentication and Dynamic Database for Free
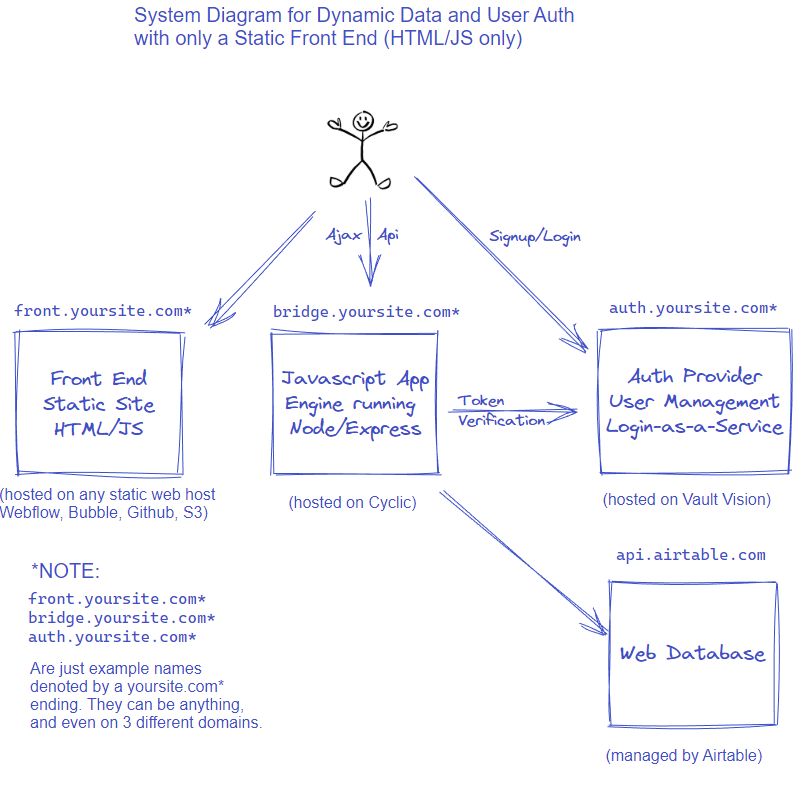 How I built a functional static web app with user authentication and dynamic database for FREE using Webflow, Vault Vision, Cyclic and Airtable with #LowCode
How I built a functional static web app with user authentication and dynamic database for FREE using Webflow, Vault Vision, Cyclic and Airtable with #LowCode
56. OAuth 2.0 for Dummies
 OAuth 2.0 is the industry-standard protocol for authorization.
OAuth 2.0 is the industry-standard protocol for authorization.
57. A Brief History in Authentication
 Photo Credits: Edward Tin
Photo Credits: Edward Tin
58. How to Add a Social Login to Your Website with SuperTokens (Custom UI Only)
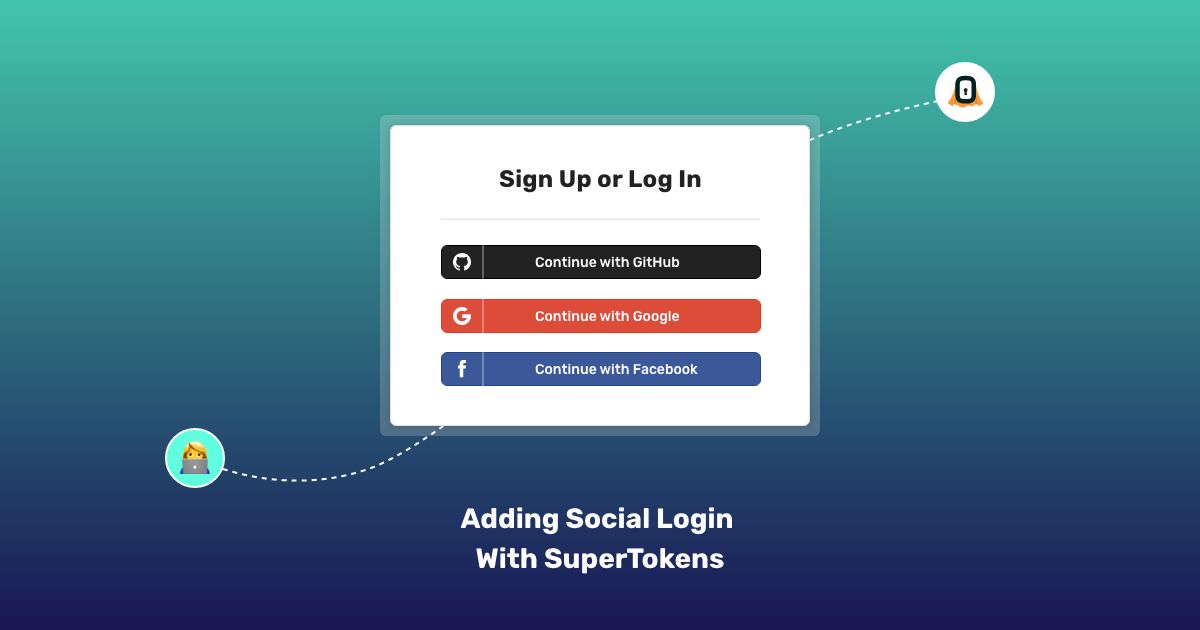 This tutorial walks you through integrating your frontend with social login APIs provided by SuperTokens.
This tutorial walks you through integrating your frontend with social login APIs provided by SuperTokens.
59. How Face ID and Touch ID Work: A Gentle Introduction to WebAthn
 The Web Authentication API (also known as WebAuthn) is an API that enables strong authentication with public-key cryptography and passwordless authentication.
The Web Authentication API (also known as WebAuthn) is an API that enables strong authentication with public-key cryptography and passwordless authentication.
60. Using Session Cookies Vs. JWT for Authentication
 HTTP is a stateless protocol and is used to transmit data. It enables the communication between the client side and the server side. It was originally established to build a connection between web browsers and web servers.
HTTP is a stateless protocol and is used to transmit data. It enables the communication between the client side and the server side. It was originally established to build a connection between web browsers and web servers.
61. Adding Auth Flow Using SuperTokens into a React and Hasura GraphQL App

62. Digital Authentication: Notes on The Road To Passwordless Authentication
 An introduction to the most popular authentication strategies along with some emerging solutions.
An introduction to the most popular authentication strategies along with some emerging solutions.
63. HMAC and MAC Explained: How To Build Secure Authentication With JWTs
 HMACs and MACs are authentication codes and are often the backbone of JWT authentication systems. Let's take a look at how they work!
HMACs and MACs are authentication codes and are often the backbone of JWT authentication systems. Let's take a look at how they work!
64. MFA Vs. 2FA: Which Is Better And More Secure

65. How Big Tech is Working Towards a Password-Free Future

66. How To Add Authentication To Your Apps and dApps
 I co-founded a developer toolkit company with the explicit goal of making decentralized applications easier to use. However, the tools aren't just for decentralized applications. Traditional application developers can make use of SimpleID to add authentication and storage to their app quickly and with zero overhead. Let me show you how easy it is.
I co-founded a developer toolkit company with the explicit goal of making decentralized applications easier to use. However, the tools aren't just for decentralized applications. Traditional application developers can make use of SimpleID to add authentication and storage to their app quickly and with zero overhead. Let me show you how easy it is.
67. How to Build an Authentication Flow with React Navigation v5
 In this tutorial I will be building two screens i.e. a signup screen and a signin screen using react navigation v5
In this tutorial I will be building two screens i.e. a signup screen and a signin screen using react navigation v5
68. How Does HTTP Authentication Work
 HTTP provides a general framework for access control and authentication. The most common HTTP authentication is based on the
"Basic" schema. This page shows an introduction to the HTTP framework
for authentication and shows how to restrict access to your server using the HTTP "Basic" schema.
HTTP provides a general framework for access control and authentication. The most common HTTP authentication is based on the
"Basic" schema. This page shows an introduction to the HTTP framework
for authentication and shows how to restrict access to your server using the HTTP "Basic" schema.
69. Connecting an Apigee Edge API Proxy with Auth0 Platform
 In the step by step tutorial learn how to use external OAuth for authentication & Access token created by the external system to secure APIGEE edge
In the step by step tutorial learn how to use external OAuth for authentication & Access token created by the external system to secure APIGEE edge
70. Alternatives to Identityserver4: What are the Best Options and the Near Future of Identityserver
 IdentityServer4 will have a new licensing policy in 2022. What should you expect from such drastic changes?
IdentityServer4 will have a new licensing policy in 2022. What should you expect from such drastic changes?
71. Implement Authentication & Security Using SuperTokens in Your React and HarperDB App

72. How To Implement Facebook Authentication And Authorization In Server-Side Blazor App
 Introduction
Introduction
73. Authentication and Authorization with bcrypt In Rails

74. .NET Authentication Security Notes
 In this article, we discuss how to protect users' authentication and session in .net, as well as Identity Server configuration.
In this article, we discuss how to protect users' authentication and session in .net, as well as Identity Server configuration.
75. How to Build Software With Low Vendor Lock-in
 We discuss some thought processes on how vendors can build software with low vendor lock-in.
We discuss some thought processes on how vendors can build software with low vendor lock-in.
76. Deploying SuperTokens with React and NodeJS on Vercel
 This tutorial will guide you on how to add SuperTokens to a React and Express app deployed on Vercel
This tutorial will guide you on how to add SuperTokens to a React and Express app deployed on Vercel
77. How to Streamline your Login Experience via Passwordless SSO
 Using YooniK technology to create a passwordless single sign-on experience using the OpenID Connect protocol.
Using YooniK technology to create a passwordless single sign-on experience using the OpenID Connect protocol.
78. Authentication Middleware in Express Gateway using JWT

79. Firebase Auth using Facebook Log-In in Expo, React Native
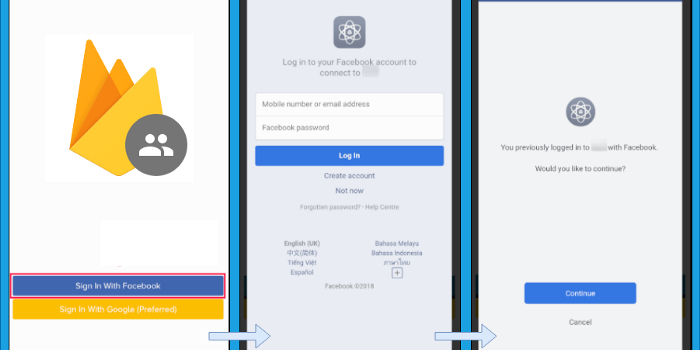 Originally published on melvinkoh.me
Originally published on melvinkoh.me
80. No Password is Better than A Strong Password
 Passwords have been on the decline for more than a decade. But eventually, we will face a time when it is no longer proof of our digital self.
Passwords have been on the decline for more than a decade. But eventually, we will face a time when it is no longer proof of our digital self.
81. Authorization With User Roles (RBAC)
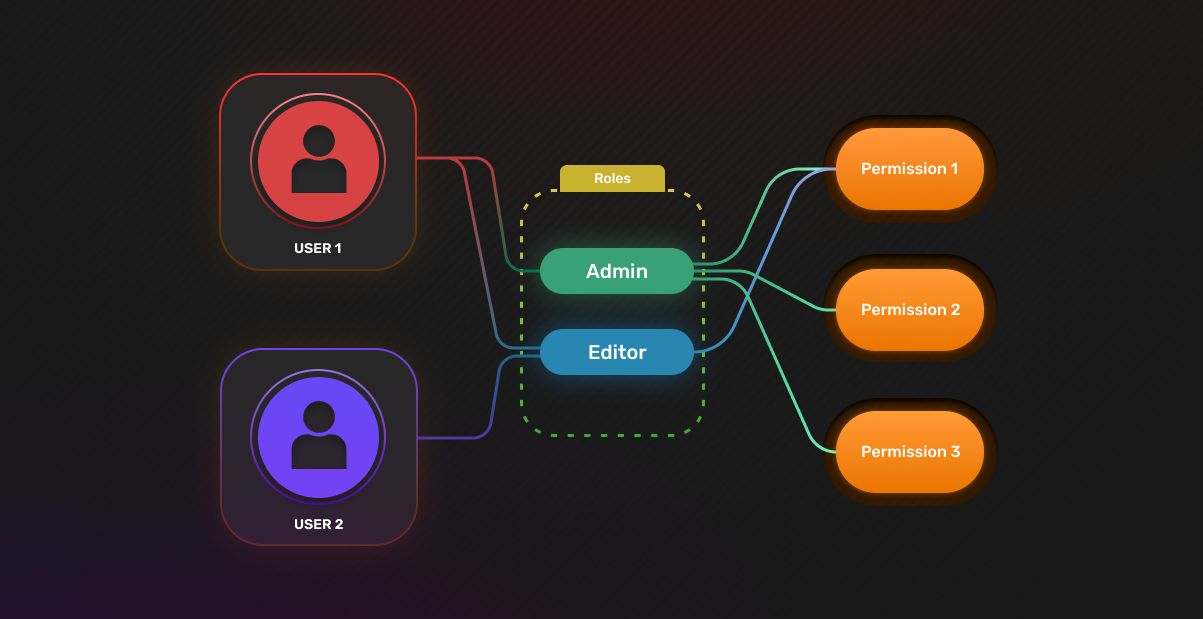 Authorization is all about answering the question “Is this user allowed to do a certain operation?”. In this post we go over how you can implement RBAC
Authorization is all about answering the question “Is this user allowed to do a certain operation?”. In this post we go over how you can implement RBAC
82. Common Attack Vectors that Authentication Services are Faced With
 Hacking user accounts on many websites is still easier than it could and should be. This blog post helps you secure your application against identity theft.
Hacking user accounts on many websites is still easier than it could and should be. This blog post helps you secure your application against identity theft.
83. Implementing Google Authentication and Fetching Mails from Scratch Using Python Django
 Google Authentication and Fetching mails from scratch means without using any module which has already set up this authentication process.
Google Authentication and Fetching mails from scratch means without using any module which has already set up this authentication process.
84. The Achilles Heel of Authentication in 2020

85. The History of Biometric Technology: From 1960 - 2020
 Modern biometric technology began in the 1960s, evolving into
high-tech scanners that read bio-markers with an accuracy touching
100%.
Modern biometric technology began in the 1960s, evolving into
high-tech scanners that read bio-markers with an accuracy touching
100%.
86. Authentication in an Angular Application Using Supabase
 Application example built with Angular 14 with authentication using the Supabase service.
Application example built with Angular 14 with authentication using the Supabase service.
87. How to Authenticate With OpenID Connect and Apache APISIX
 In this post, I want to demo how to use OpenID Connect using Google underneath and then switch to Azure.
In this post, I want to demo how to use OpenID Connect using Google underneath and then switch to Azure.
88. Setting up 2FA on 9 Popular Apps & Services Before Safer Internet Day
 How to enable 2FA and what is two-factor authentification is. Set it up before Safety Internet Day which is celebrated on February 8 and make you apps secure
How to enable 2FA and what is two-factor authentification is. Set it up before Safety Internet Day which is celebrated on February 8 and make you apps secure
89. Do Passwordless Technologies Have an Impact on Cybersecurity?
 Contrary to popular belief, traditional passwords are not the best way to protect sensitive information on our digital devices.
Contrary to popular belief, traditional passwords are not the best way to protect sensitive information on our digital devices.
90. Security Best Practices for Node.js Apps

Node.js Security Guide
91. Express.js Integration Guide for Passwordless Authentication with DID.app
 Just want the code? Find this example on github
Just want the code? Find this example on github
92. Creating a Middleware in Golang for JWT based Authentication

93. Authentication using the Amazon Cognito to an Angular application
 Application example built with Angular 14 with authentication using the Amazon Cognito service.
Application example built with Angular 14 with authentication using the Amazon Cognito service.
94. Revoking Access to JWT tokens with a Blacklist/Deny List
 Learn how to maintain a JWT blacklist / deny list using an in-memory data cache.
Learn how to maintain a JWT blacklist / deny list using an in-memory data cache.
95. How To Create User Profile Page for E-Commerce Android App
 We are going to create an android UI for our UserProfile backend API we are creating for our demo E-commerce tutorial
We are going to create an android UI for our UserProfile backend API we are creating for our demo E-commerce tutorial
96. 3 Reasons for B2C Enterprises to Implement Single Sign-on Authentication
 Single sign-on authentication, or SSO, is becoming more commonplace as the digital revolution continues to evolve. With numerous benefits for customers and companies alike, SSO helps streamline user experience, aid movement between applications and services, and secure the transfer of pertinent information about customers between organizations.
Single sign-on authentication, or SSO, is becoming more commonplace as the digital revolution continues to evolve. With numerous benefits for customers and companies alike, SSO helps streamline user experience, aid movement between applications and services, and secure the transfer of pertinent information about customers between organizations.
97. 80% Devices in 2023 Are Already Passkey-Ready: Apple, Microsoft, and Google Pushing It Even Higher
 Since the 3 digital leaders, Apple, Google, and Microsoft, are pushing passkeys as the new login standard, the current technical support for passkeys is high
Since the 3 digital leaders, Apple, Google, and Microsoft, are pushing passkeys as the new login standard, the current technical support for passkeys is high
98. Implementing Social Login for a React and Backend App
 Implementing Social Login: A Step-by-Step Guide in React with Typescript. How to add Github and Google login for users and taking advantage of the social netwo
Implementing Social Login: A Step-by-Step Guide in React with Typescript. How to add Github and Google login for users and taking advantage of the social netwo
99. How Law Enforcement Agencies are Using Biometrics
 Here's why law enforcement agencies like the FBI and police use biometric technology to enhance their security and to protect them from unauthorized access.
Here's why law enforcement agencies like the FBI and police use biometric technology to enhance their security and to protect them from unauthorized access.
100. Poor Man’s Authorization: How to Implement RBAC for REST API with OPA
 When it comes to application permissions, two results emerge from this situation:
When it comes to application permissions, two results emerge from this situation:
101. So, Like, What is an API Key Really? And How Does it Provide Security?
 An API key is a secret code that gets you inside. Yeah it does!
An API key is a secret code that gets you inside. Yeah it does!
102. AssumeRoleWithWebIdentity WHAT?! Debugging the Github to AWS OIDC InvalidIdentityToken Failure Loop
 We encountered the InvalidIdentityToken error with the AssumeRoleWithWebIdentity method - we'll dive into how to fix it.
We encountered the InvalidIdentityToken error with the AssumeRoleWithWebIdentity method - we'll dive into how to fix it.
103. Bringing Top 5 Unconventional Identity Verification Solutions to The Table
 Enterprises must not think twice before integrating themselves with AI-powered online identity verification processes to combat chargeback, counterfeits
Enterprises must not think twice before integrating themselves with AI-powered online identity verification processes to combat chargeback, counterfeits
104. About Kubernetes Authentication

105. What is Single Sign-On about?
 We hate filling out forms, right? What if we can skip it? Thanks to single sign-on, it is possible.
We hate filling out forms, right? What if we can skip it? Thanks to single sign-on, it is possible.
106. How Routee's Two Factor Authentication Works
 Two Factor Authentication or Two Factor Verification is a service used to confirm a user’s identity by combining two different elements. For example, Routee service combines a unique code with a verified phone number. This service can be used as part of an app or a website sign up process to increase security for the services offered.
Two Factor Authentication or Two Factor Verification is a service used to confirm a user’s identity by combining two different elements. For example, Routee service combines a unique code with a verified phone number. This service can be used as part of an app or a website sign up process to increase security for the services offered.
107. Could a Decentralized Login Have Prevented @Jack's Hack?
 A possible solution to single-factor and multi-factor authentication methodologies using decentralized login (DLI).
A possible solution to single-factor and multi-factor authentication methodologies using decentralized login (DLI).
108. One-Time Password Generation Using speakeasy, Nest.js And MongoDB
 Here, we have designed and developed a flow for OTP(One time password) for user registration and also blocking a user's account after the maximum retries for incorrect otp is exceeded.
Here, we have designed and developed a flow for OTP(One time password) for user registration and also blocking a user's account after the maximum retries for incorrect otp is exceeded.
109. Authentication in React with Firebase

110. How to Configure Your Preferred User Stores to Authenticate Users using WSO2

111. How To Create A User Portal On Airtable With Sync Inc And React
 In this tutorial, you’ll see how to build a scalable, secure, and flexible client portal on Airtable using Sync Inc, Cotter, and Next.js.
In this tutorial, you’ll see how to build a scalable, secure, and flexible client portal on Airtable using Sync Inc, Cotter, and Next.js.
112. Web Auth Standard: Guide to Web Authentication API
 Secure context
This feature is available only in secure contexts (HTTPS), in some or all supporting browsers.
Secure context
This feature is available only in secure contexts (HTTPS), in some or all supporting browsers.
113. How to Customize Devise Authentication with Active Storage
 It is really difficult to imagine an application without a very secure authentication module, they vary from one to other, but almost always having common components, like a form to introduce a user name or email, their password, maybe some social media authentication, even biometric inputs.
It is really difficult to imagine an application without a very secure authentication module, they vary from one to other, but almost always having common components, like a form to introduce a user name or email, their password, maybe some social media authentication, even biometric inputs.
114. Configure MongoDB with Kerberos Authentication
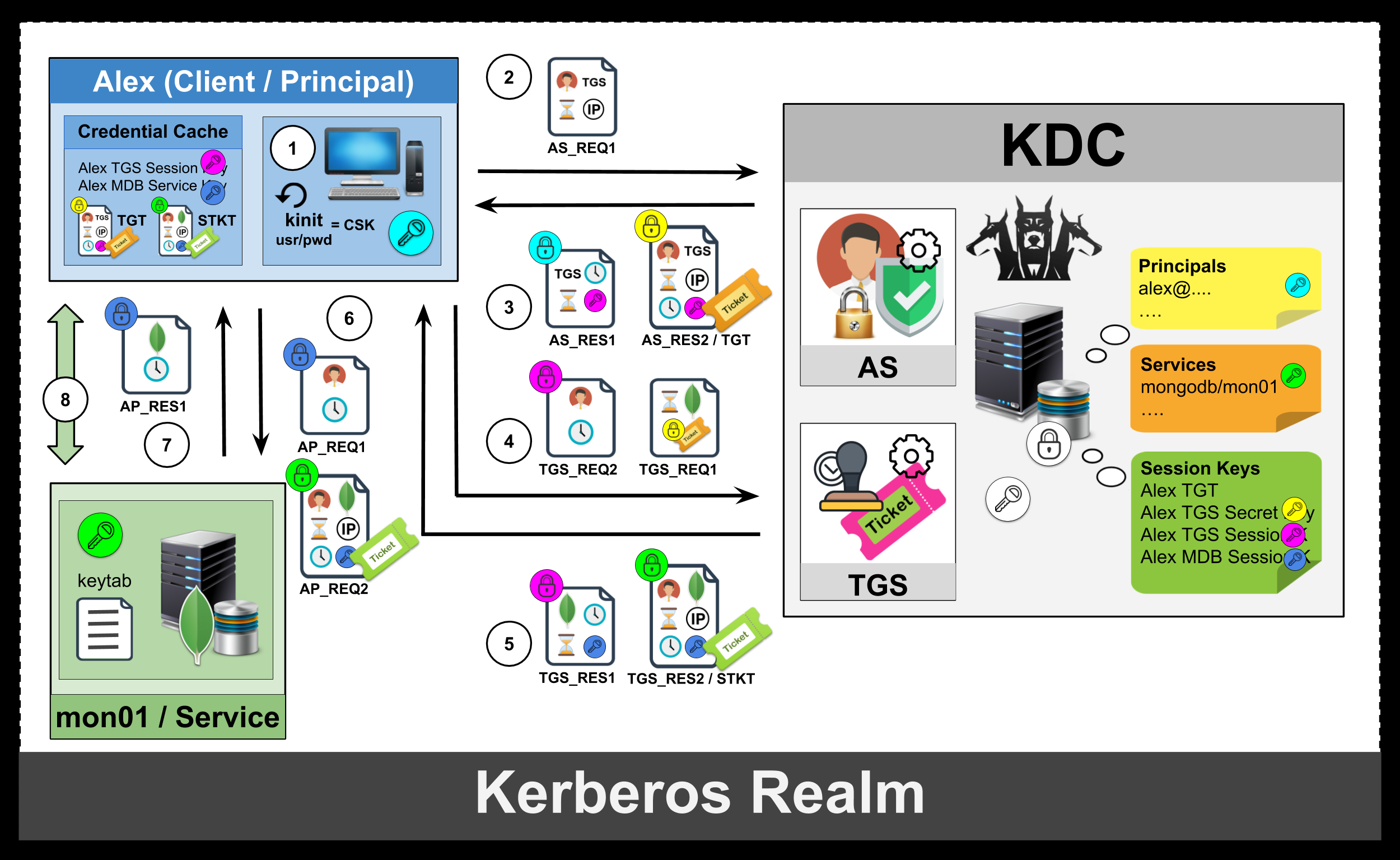 The MongoDB database administrators in a large enterprise may need to configure MongoDB to support Kerberos Authentication. The configuration of MongoDB with Kerberos authentication is very simple, provided you have some Kerberos knowledge. The MongoDB documentation article, Configure MongoDB with Kerberos Authentication on Linux, is pretty extensive on this topic. However, the article states — “Setting up and configuring a Kerberos deployment is beyond the scope of this document”, resulting in some of the starters/enthusiasts with limited knowledge in Kerberos not proceed any further. This article is geared more towards bridging that gap and to help you understand
The MongoDB database administrators in a large enterprise may need to configure MongoDB to support Kerberos Authentication. The configuration of MongoDB with Kerberos authentication is very simple, provided you have some Kerberos knowledge. The MongoDB documentation article, Configure MongoDB with Kerberos Authentication on Linux, is pretty extensive on this topic. However, the article states — “Setting up and configuring a Kerberos deployment is beyond the scope of this document”, resulting in some of the starters/enthusiasts with limited knowledge in Kerberos not proceed any further. This article is geared more towards bridging that gap and to help you understand
115. How To Improve Banking App Security With GPS Data
 Mobile-based fintech solutions are becoming the first port of call for many financial services, as people embrace the simplicity, cost-effectiveness and speed of mobile payments. However, digital fraud is rising as fast, if not faster, and thus fraud monitoring based on robust customer authentication have become as important as the services mCommerce has to offer customers.
Mobile-based fintech solutions are becoming the first port of call for many financial services, as people embrace the simplicity, cost-effectiveness and speed of mobile payments. However, digital fraud is rising as fast, if not faster, and thus fraud monitoring based on robust customer authentication have become as important as the services mCommerce has to offer customers.
116. Basic Elixir Api Guide
 Elixir represents relatively new programming language for wider audience. It was published back in 2011, and is in development ever since. His main trait is that adops functional pardigm because it is built on top of Erlang and runs on BEAM(Erlang VM).
Elixir represents relatively new programming language for wider audience. It was published back in 2011, and is in development ever since. His main trait is that adops functional pardigm because it is built on top of Erlang and runs on BEAM(Erlang VM).
117. UMA (User-Managed Access) 2.0: How It Works And What It Can Be Used For
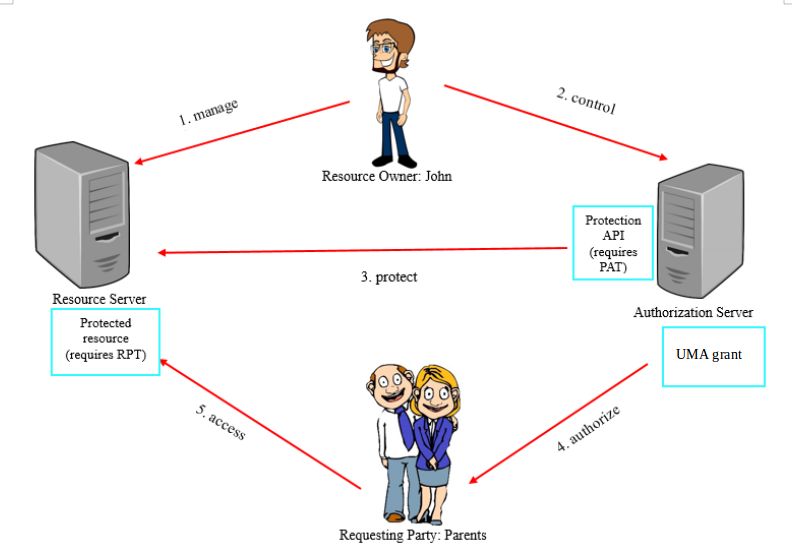 User-Managed Access (UMA) is an OAuth-based access management protocol standard. Introduction to UMA and where it can be used.
User-Managed Access (UMA) is an OAuth-based access management protocol standard. Introduction to UMA and where it can be used.
118. Hashing, Salting, and Verifying Passwords in NodeJS, Python, Golang, and Java
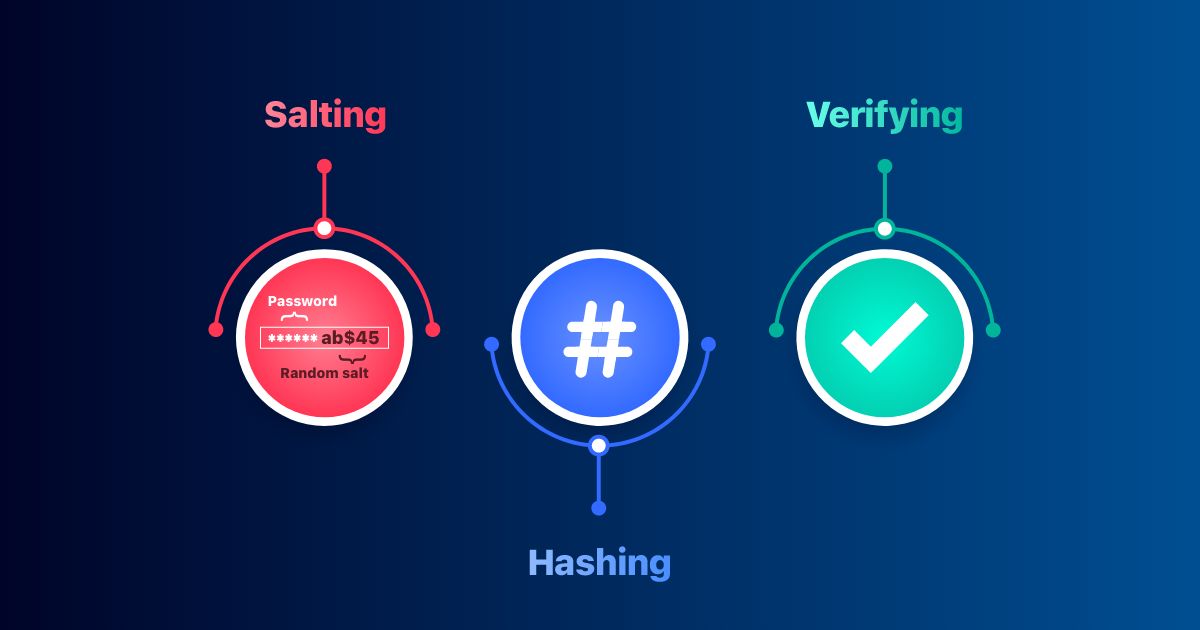 How to hash and salt passwords in different languages and why it's important to do so
How to hash and salt passwords in different languages and why it's important to do so
119. Learnings From The Meow Bot Attack on Our MongoDB Databases

120. The Business Costs of Compromised Passwords
 Passwords and Their Ability to Bring Down Even the Largest of Enterprises
Passwords and Their Ability to Bring Down Even the Largest of Enterprises
121. Setting Up Authentication for AWS EKS
 Amazon Elastic Kubernetes Service (EKS) is one of the leading managed Kubernetes solutions.
Amazon Elastic Kubernetes Service (EKS) is one of the leading managed Kubernetes solutions.
122. Building an Airtight Security Funnel Step-by-Step
 In this article, we’ll walk through SharePass’s patent-pending security funnel, providing a step-by-step guide to building out your security pipeline.
In this article, we’ll walk through SharePass’s patent-pending security funnel, providing a step-by-step guide to building out your security pipeline.
123. Biometrics and Mobile Apps: Reducing Friction with a Focus on Security

124. Biometrics And The Future Of Tracking
 Almost any organization experiences one of the main problems with the personnel policy - personnel discipline. It is particularly relevant for large companies. Here are several unpleasant consequences that this problem leads to. First of all, these are quite tangible hidden costs due to insufficient production of goods and services, foregone turnover, loss of important customers, and other losses from the irrational use of working time by employees. Let's say an employee takes 15-20 extra minutes every day to be late, protract a lunch break, have smoke breaks, go home early, and other things. Shouldn't be too hard to calculate that eventually it all takes an entire working day from one working month. In reality, people spend much more working time on personal needs: up to 35%.
Almost any organization experiences one of the main problems with the personnel policy - personnel discipline. It is particularly relevant for large companies. Here are several unpleasant consequences that this problem leads to. First of all, these are quite tangible hidden costs due to insufficient production of goods and services, foregone turnover, loss of important customers, and other losses from the irrational use of working time by employees. Let's say an employee takes 15-20 extra minutes every day to be late, protract a lunch break, have smoke breaks, go home early, and other things. Shouldn't be too hard to calculate that eventually it all takes an entire working day from one working month. In reality, people spend much more working time on personal needs: up to 35%.
125. Using OAuth Authentication to Serve Static Internal Documentation
 Let's walk through how to deploy Docusaurus behind an OAuth proxy which will force users to log in with a 3rd party provider before viewing our documentation.
Let's walk through how to deploy Docusaurus behind an OAuth proxy which will force users to log in with a 3rd party provider before viewing our documentation.
126. Auth in a React App with AWS: How Does It Really Work?
 For this Tech Stack in 10, I'm diving into some best practices for using authentication in your full stack application with AWS Cognito, DynamoDB, and AppSync.
For this Tech Stack in 10, I'm diving into some best practices for using authentication in your full stack application with AWS Cognito, DynamoDB, and AppSync.
127. Digital Signatures in Cryptography: Types, Applications, Process

128. Authentication Vs. Authorization [Infographic]

129. How To Protect Your Online Applications From Pass-the-Cookie Cyber Attacks
 How to strengthen your online apps against cloud service attacks such as ‘pass-the-cookie’ attacks.
How to strengthen your online apps against cloud service attacks such as ‘pass-the-cookie’ attacks.
130. Authentication Tools For Developers: A Comparison
 When I first started learning to code, I went through more tutorials than I can count. I built so many todo list apps that I can’t even use a todo list without wondering if someone built it as a tutorial then turned it into a product. I learned CRUD (create, read, update, delete). I learned frameworks (React, Angular, Vue). I learned so much, but in every tutorial, something was missing. Something critical.
When I first started learning to code, I went through more tutorials than I can count. I built so many todo list apps that I can’t even use a todo list without wondering if someone built it as a tutorial then turned it into a product. I learned CRUD (create, read, update, delete). I learned frameworks (React, Angular, Vue). I learned so much, but in every tutorial, something was missing. Something critical.
131. 4 Dangers of Sticking with Outdated MFA Methods
 Adopting Multifactor Authentication is just the start of securing your digital systems, but outdated MFA methods can still present vulnerabilities if unchecked.
Adopting Multifactor Authentication is just the start of securing your digital systems, but outdated MFA methods can still present vulnerabilities if unchecked.
132. How You Can Add Multi-Factor Authentication To Your Application
 In light of countless security breaches across the industry, multi-factor authentication is becoming increasingly popular. Let's look at the available options!
In light of countless security breaches across the industry, multi-factor authentication is becoming increasingly popular. Let's look at the available options!
133. How to Implement a Forgot Password Flow (With Pseudo Code)
 What should happen on the backend when a user forgets their password? Read to find a pseudo code implementation of the simplest way to reset passwords securely.
What should happen on the backend when a user forgets their password? Read to find a pseudo code implementation of the simplest way to reset passwords securely.
134. Biometric Authentication - Working, Methods, and Use Cases
 Biometrics is a scientific term for the physical or behavioral characteristics of humans. Biometric authentication is biometrically enabled data protection.
Biometrics is a scientific term for the physical or behavioral characteristics of humans. Biometric authentication is biometrically enabled data protection.
135. NFTs for Authorized User Registration - Part 2
 How can NFTs be used as part of an authorized user registration? Here's how.
How can NFTs be used as part of an authorized user registration? Here's how.
136. Building a Login Screen With React and Bootstrap
 Build an elegant login screen super fast using React and Bootstrap
Build an elegant login screen super fast using React and Bootstrap
137. Best Practises For Protecting Your Email
138. An In-Depth Comparison of OAuth and JWT (JSON Web Tokens)
 Learn about the difference between JWT Token and OAuth
Learn about the difference between JWT Token and OAuth
139. How to Execute a Scheduled Task in Keycloak on Startup
 In this article, we will look at how to execute a scheduled task in Keycloak on startup using a Kafka consumer as an example.
In this article, we will look at how to execute a scheduled task in Keycloak on startup using a Kafka consumer as an example.
140. How Zero Trust Vendors are Concealing the Truth About This Robust Mechanism?
 With the increasing cybersecurity risks and breaches in the past couple of years, businesses are now moving with a clear vision to incorporate zero-trust architecture into their platforms.
With the increasing cybersecurity risks and breaches in the past couple of years, businesses are now moving with a clear vision to incorporate zero-trust architecture into their platforms.
141. How To Improve Your Signup Flows

142. You Probably Don't Need OAuth2/OpenID Connect: Here's Why
 And the great news is, if the need for OAuth2 and OpenID Connect arises, you can use Ory again to add these on top!
And the great news is, if the need for OAuth2 and OpenID Connect arises, you can use Ory again to add these on top!
143. Firebase Authentication with Email and Password in Flutter
 Make use of Firebase Cloud Functions and Firestore to Authenticate in Flutter. SingInWithEmailAndPassword, HTTP Callables and Trigger, and more.
Make use of Firebase Cloud Functions and Firestore to Authenticate in Flutter. SingInWithEmailAndPassword, HTTP Callables and Trigger, and more.
144. Identity Governance: Why Enterprises Don’t Implement It?
 Maintaining the digital environment of an enterprise is a complex task and it takes more than technology to make things right. Businesses are in continuous need of regulatory controls like identity governance to maintain their brand value and simultaneously control their resources.
Maintaining the digital environment of an enterprise is a complex task and it takes more than technology to make things right. Businesses are in continuous need of regulatory controls like identity governance to maintain their brand value and simultaneously control their resources.
145. Overriding the SuperTokens APIs for Custom Usecases
 In this blog we discuss how to customize the auth APIs provided by SuperTokens using its “Override” feature"
In this blog we discuss how to customize the auth APIs provided by SuperTokens using its “Override” feature"
146. Authentication in Web Apps: Connecting Auth0, ASP.NET Core and Nuxt.js
 User authentication and authorization can be difficult and time consuming. Getting it wrong can also have disastrous consequences, such as malicious users accessing and stealing personal or sensitive information from your app.
User authentication and authorization can be difficult and time consuming. Getting it wrong can also have disastrous consequences, such as malicious users accessing and stealing personal or sensitive information from your app.
147. Introduction to Cryptography: Vigenère Cipher [Part 2]
 Hi again and welcome back to part 2 of the basic cryptography. Previously we discuss about what is cryptography and how fundamental and ancient problem it is in communication science. We talk about ceaser's cipher and how easy it is to break. We also talk about Substitution Cipher which was slight improvement to Ceaser' cipher but can easily be cracked using Frequency analysis technique.
Hi again and welcome back to part 2 of the basic cryptography. Previously we discuss about what is cryptography and how fundamental and ancient problem it is in communication science. We talk about ceaser's cipher and how easy it is to break. We also talk about Substitution Cipher which was slight improvement to Ceaser' cipher but can easily be cracked using Frequency analysis technique.
148. JSON Web Auth Using Angular 8 and NodeJS

149. Ensuring Security: A Guide for Web and Mobile Application Development
 Authentication and authorization for modern web and mobile applications are a key part of most development cycles. This story outlines some considerations.
Authentication and authorization for modern web and mobile applications are a key part of most development cycles. This story outlines some considerations.
150. Introduction to IDaaS and its Applications
 If you're reading this article, you might be interested to learn how to implement user management for your application, understanding the complete picture of how identity management services work. That's what we'll do in this article. You'll learn what is Identity as a Service (IDaaS), why to use such a service, what is Single Sign-On (SSO), and IDaaS platforms.
If you're reading this article, you might be interested to learn how to implement user management for your application, understanding the complete picture of how identity management services work. That's what we'll do in this article. You'll learn what is Identity as a Service (IDaaS), why to use such a service, what is Single Sign-On (SSO), and IDaaS platforms.
151. The Pain Of Making A Blockchain App From Scratch
 So easy, an ape could do it. Thoughts from the lead developer and Top Ape at SnowApe, a Web3 real money gaming project that made a blockchain app from scratch.
So easy, an ape could do it. Thoughts from the lead developer and Top Ape at SnowApe, a Web3 real money gaming project that made a blockchain app from scratch.
152. Why IAM Architects Prescribe Enterprise Application Security
 The widespread use of modern applications by enterprises come at a cost of data breaches. For this reason, Identity and access management or IAM architects have
The widespread use of modern applications by enterprises come at a cost of data breaches. For this reason, Identity and access management or IAM architects have
153. Authenticate Users Via Face Recognition On Your Website or App
 Learn how to authenticate users on a typical website or web application via face recognition instead of the traditional login/password pair.
Learn how to authenticate users on a typical website or web application via face recognition instead of the traditional login/password pair.
154. The Difference Between OAuth 2.0 And Session Management
 There seems to be a lot of misinformation on when OAuth 2.0 (henceforth referred to as OAuth) is appropriate for use. A lot of developers confuse OAuth with web session management and hence end up using the wrong protocol / set of technologies. This, in turn, leads to security issues. This article will clarify when to use regular session management solutions and when to use any one of the OAuth flows.
There seems to be a lot of misinformation on when OAuth 2.0 (henceforth referred to as OAuth) is appropriate for use. A lot of developers confuse OAuth with web session management and hence end up using the wrong protocol / set of technologies. This, in turn, leads to security issues. This article will clarify when to use regular session management solutions and when to use any one of the OAuth flows.
155. How to Properly Authenticate Your Emails
 Learn what email authentication is and how to authenticate your email properly using email authentication protocols such as SPF, DKIM and DMARC.
Learn what email authentication is and how to authenticate your email properly using email authentication protocols such as SPF, DKIM and DMARC.
156. NFTs for Authorized User Registration - Part 1
 How does using an NFT as part of an MFA login work? Here's how.
How does using an NFT as part of an MFA login work? Here's how.
157. The Ultimate Guide To Custom Role Based Access Without Third Party Libraries

158. Configuring Single Sign-On for Zoom With WSO2 Identity Server

159. The HackerNoon Podcast: Let's Talk About Sec, Baby
 Amy Tom talks to Jeff Morris, VP of Product & Solutions Marketing at Couchbase, and Mike Schwartz, Founder & CEO of Gluu on The HackerNoon Podcast
Amy Tom talks to Jeff Morris, VP of Product & Solutions Marketing at Couchbase, and Mike Schwartz, Founder & CEO of Gluu on The HackerNoon Podcast
160. Validating a User Phone Number With SMS on Auth0 Using ZENVIA
 Application example using Angular where a simple WEB application will be implemented to validate the user phone by SMS in the authentication.
Application example using Angular where a simple WEB application will be implemented to validate the user phone by SMS in the authentication.
161. A React HOC for AWS Cognito to Simplify User Authentication
 TL;DR: AWS Cognito offers robust handling of user Authentication flows, including via Social Providers such as Google and Facebook. Here we describe a Higher Order Component for your ReactJS Web App, and how to configure Cognito.
TL;DR: AWS Cognito offers robust handling of user Authentication flows, including via Social Providers such as Google and Facebook. Here we describe a Higher Order Component for your ReactJS Web App, and how to configure Cognito.
Thank you for checking out the 161 most read stories about Authentication on HackerNoon.
Visit the /Learn Repo to find the most read stories about any technology.

